The next generation of online authentication
In the last twelve months, if you, your corporation or institution has not been victim of a cyber security attack, there can only be two reasons. Either you are complying with a comprehensive and user-friendly security strategy or you have simply been very lucky.
By: Michael Armentrout, Regional Marketing Manager Infineon & FIDO Board Representative and Anasthasia Westphal, Product Marketing Manager Infineon & Member of the FIDO Europe Working Group (FEWG)
Password security, or the lack thereof, is at the very heart of the increasing threat to cyber security and many online service providers are still not properly enforcing effective authentication.
To put it in more provocative terms: The next generation of online authentication seeks to provide better security mechanism as passwords alone due to the fact that even the smartest password without a hardware-based second factor can be attacked, eventually.
The continuous problem with passwords
Passwords are still the first line of defence for most online services. Regrettably, often they are not sufficient. $16bn were stolen from 15.4 million victims in the US alone through identity fraud in 2016. [1] Problems caused by the reliance on single-factor password authentication have actually increased in the last years. According to Verizon’s 2017 Data Breach Investigation Report, 81% of attack-related data breaches in the last year could be attributed to stolen or guessable passwords - up from 66% in 2016.
This is not surprising, considering that many users are still careless when choosing appropriate passwords. Forbes reported that the most popular passwords in North America and Western Europe in 2016 were, for the third year running, “123456” and “password”. [2] The common practice of reusing passwords for different sites also means that an online service’s security may rely on the security level of other sites where the password is used.
Unfortunately, even if a user selected unique, strong passwords for all of their accounts, due to social engineering and sophisticated phishing algorithms, passwords often still remain the weakest link in a security system.
[1] https://www.javelinstrategy.com/press-release/identity-fraud-hits-record-high-154-million-us-victims-2016-16-percent-according-new
[2] https://www.forbes.com/sites/ygrauer/2017/01/23/2016s-worst-passwords-are-just-as-bad-as-2015s-so-please-tell-me-yours-is-not-on-the-list/#38fe9e363387
An alliance of the most powerful players in the industry
Online service providers need a stronger form of authentication. While some have worked in silos to develop proprietary solutions, 'locking' the user to a proprietary implementation that cannot be used on other platforms, many companies have come together to develop an industry standard for authentication.
The technology industry’s response to these developments is the FIDO Alliance, a non-profit consortium founded in 2013 by, amongst others, PayPal and Infineon Technologies. FIDO stands for 'Fast IDentity Online' and its specifications support different authentication technologies and communication standards with the aim to create a single open standard for stronger authentication, which will run across all FIDO services - a single device which supports them all.
The FIDO ecosystem enables better security for online services, reduces cost for the deploying enterprise authentication, and an easier consumer experience. Four years after the initial launch, the Alliance has expanded massively to 250 member companies across many industry sectors, including Google, Samsung, Visa, Docomo, Microsoft, Amazon and many other commercial companies and governmental organisations. In 2016, the number of FIDO certified solutions grew by 200% to more than 300 products from over 100 organisations.
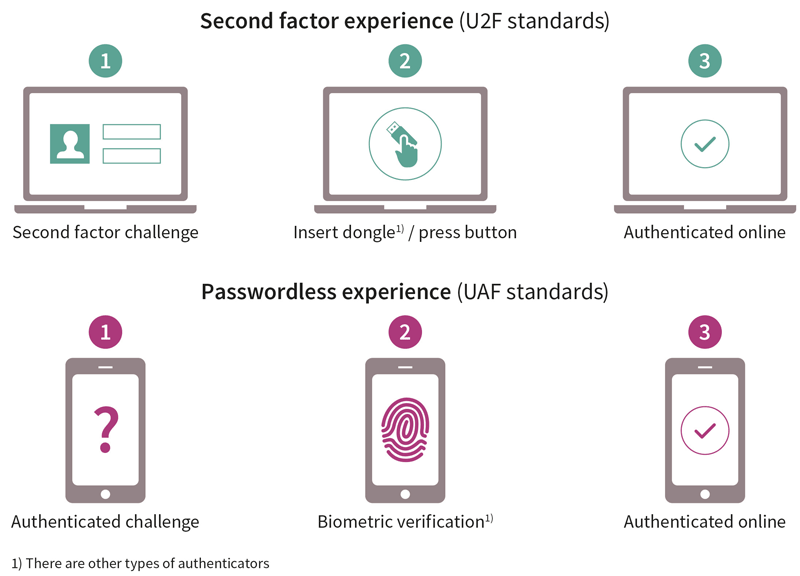
The FIDO Alliance has delivered a comprehensive framework of open industry standards for simpler and stronger authentication. The FIDO specifications and certifications enable an interoperable ecosystem of hardware-, mobile-, and biometrics-based authenticators that can be used across various hardware and software platforms, apps and websites. FIDO currently offers two sets of authentication specifications: The Universal Authentication Framework (UAF) programme and the second factor Universal Second Factor (U2F) programme.
Benefits of using a security key
There are many companies deploying FIDO today, taking advantage of the benefits FIDO offers while operating on a hardware-based security chip. Cloud service providers such as Google, Salesforce, Dropbox, GitHUb, Bitbucket, and Sentry use the FIDO U2F protocol with hardware-based tokens. Facebook, with its two billion users, has taken account protection to the next level with Security Key, a token-based U2F solution that works well for users that don’t want a phone-back up.
An increasing number of web browsers that are also supporting U2F include Googles Chrome and Opera. Financial organisation, healthcare organisations and enterprises will also benefit from an open, authentication standard. Governments have already started with implementations: U2F authentication is used, for example, by the government in Great Britain to allow its citizens to securely access the GOV.UK verify public digital services.
Why use a solution that requires a hardware token? The answer convinces more and more relying parties: an out-of-band hardware security key is simple to implement and deploy, easy to use, private and, most importantly, provides hardened security. Compared to authentication technologies using OTPs (via SMS 2FA) or mobile phone apps, U2F a hardware-based deployment is much faster and requires less support cost.
Infineon supplies the intelligence
As a leading supplier of security controller technologies used to protect personal identity and computer data, Infineon offers a wide portfolio of products combined with exceptional expertise in the implementation of hardware-based security solutions. As founding member and board member of the FIDO Alliance, Infineon is an active contributor to the development of new specifications.
The Munich-based technology corporation was one of the first suppliers of security chips to offer FIDO-certified authenticator reference designs for secured devices and now has wide implementation experience with customer specific designs for multiple authenticator form factors.
Infineon has released three FIDO U2F Certified reference designs to enable fast and easy implementation of the FIDO standard for authentication tokens: Infineon U2F HID Reference Design, V2; SLE78 U2F NFC Reference Design and the Infineon U2F BLE Authenticator Reference Design.
Providing security products for various applications, Infineon and the related Infineon products are well suited to target the high security levels demanded by many FIDO deployments. The security chip is Common Criteria certified.
Conclusion
Poor passwords and ineffective security policies have been criticised for many years, while two-factor authentication continues to be a recommended method to secure services. The danger, especially for enterprises, financial institutions and public administrations, is that dedicated attacks can easily bypass weak password systems as well as SMS second factor authentication implementations.
The additional challenge has been that any improvements to this situation often come at the cost of convenience for the user. Out-of-band hardware tokens are the best solution to this predicament. Using the FIDO open standards, enterprises and governments can help protect the user from increasing attacks and threats to online assets by implementing FIDO-based authentication solutions.