Nightmare on IoT security street
Security is becoming a major headache for IoT companies. Steve Rogerson looks at the risks. The dream of billions of connected devices comes with a security nightmare as even a small vulnerability in a cheap consumer device can lead to a massive problem. While most people are not that concerned about a minor hack on a connected fridge or kettle, the problem is what the hacker can do once connected.
Already, connected baby monitors and security cameras have been used to launch distributed denial of service (DDoS) attacks on major websites. Unless such devices along with all the new ones coming along are secured, the danger of more frequent attacks becomes very real.
Thus, many believe the only answer is regulation. To put these products on sale, it must be law to have some form of accepted security that can be updated remotely.
IoT security threat
Most IoT systems work in a similar fashion. At the edge are devices that can send and receive data and commands. Clever ones can analyse this data and act autonomously. They are all connected to some form of network that will carry the data and commands between the devices and a server that can do more in-depth analysis and send instructions.
All three layers can be attacked. A dodgy device at the edge can have fake measurements inserted that can disrupt the whole process or cause them to react inappropriately. A bad server can be used to send incorrect commands or trigger unplanned events. Eavesdroppers can listen in to all three layers to access confidential data or information on the operation of the infrastructure that could be used by a hacker.
“The other component is human interaction,” said Steve Hanna, Senior Principal for Digital Security at Infineon. “Humans want to see and control what’s going on.” The first step towards security is to do a risk analysis. Engineers have to work out what can go wrong. “This makes us some of the most paranoid people on the planet,” said Hanna.
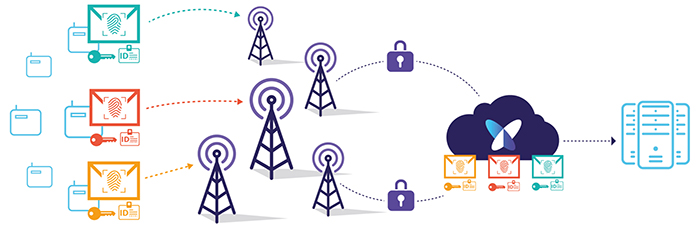
Above: Security needs to be implemented at all levels (Picture: Sigfox)
However, this is necessary, he said, as consumers are often not aware of security features and leave devices with default passwords in place. Default passwords are not hard to discover and for a mass-market item suddenly the hackers have access to thousands of connected devices that can be coordinated and used to attack websites.
“You can gather together a large number of devices and do a firmware update that inserts malware,” said Nicolas Schieli, Senior Marketing Director at Microchip. “The malware can be used to do whatever you want.” This includes a denial of service attack, which criminals use to make money.
“This is used for extortion,” said Hanna. “Pay me or I take down your site. Or it can be used for revenge. This is why governments are beginning to step forwards to demand certain minimum levels of IoT security. Due to market pressure, it will probably be regulatory efforts that drive consumer device manufacturers to adopt adequate security.”
As well as denial of service attacks, Ian Heritage, Cyber Security Architect at Trend Micro, said these could also be used for mining crypto currencies with just a small piece of software.
There is also a fear that taking control of some individual devices could have significant consequences. This has already been seen in automotive with the now infamous controlled attack on a Jeep Cherokee, where hackers remotely took control of the steering and brakes. As cars become more connected and autonomous, there is the worry that a coordinated attack on hundreds of cars could bring a city to a standstill.
There are also fears in the medical world. Devices such as insulin pumps are now becoming cloud connected, and for good reason. This lets, for example, a parent monitor the blood sugar levels of a child with diabetes. But once connected, the same devices could be used by a hacker to say, overdose the patient or disable the device with serious consequences.
“If these are hacked, it can be dangerous,” said Schieli. “They could deliver the wrong amount of insulin, for example. The cost to protect these is 30 to 50 cents per device. That is very low compared with the cost of an insulin pump, but many manufacturers believe they can get away without security.”
The FDA in the US is looking at what kinds of security it could mandate for medical devices and California has passed regulations that says those selling connected devices must make reasonable efforts to make them secure.
Defence against IoT attacks
Among the common defences against attack is having some form of authentication. “If you don’t know what or whom you are talking to, you don’t have a secure system,” said Hanna. “This can allow false data to be input into the system.” Boot protection and a way to ensure secure updates are needed.
“When you boot, you want to make sure that only the correct software is uploaded,” said Hanna. “You need constant updates to fix security vulnerabilities. There are always bugs in software and you need to eliminate them. If you do not keep them up to date, there will be toolkits on the internet to attack the devices.”
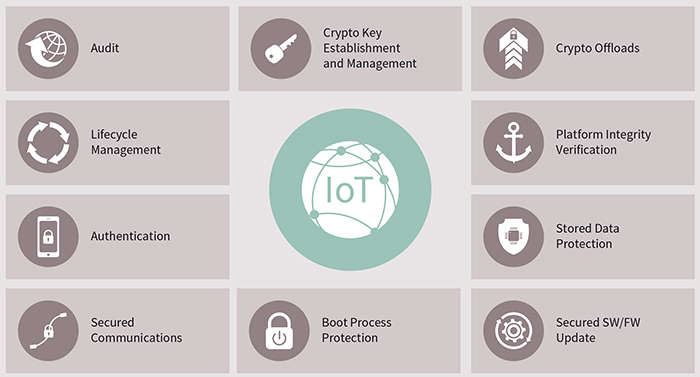
Above: Common defences against attacks on the IoT (Picture: Infineon)
While Schieli believes a simple answer is to have devices that will not work until the user changes the password from the default, he acknowledges that this will impact acceptance as many people find the technology complex enough without adding more things to do.
“The answer is to have an upgrade mechanism for the firmware that is not based on a password but on cryptography,” he said. “So you get rid of the end user in the loop. You are eliminating the human factor.”
Another issue is that devices are usually put together by lots of people in the supply chain, so security has to be implemented at every level. “You should build security in from the start,” said Heritage.
Also, confidential data needs to be protected, often through encryption. Security can be implemented in software, and that has real advantages, not least that it can be rolled out quickly. However, the best form of security is a combined hardware and software approach. “You can’t do it without software, but you need hardware to protect the cryptographic secrets and create a root of trust,” said Hanna.
IoT networking
While most of the security focus is on the devices and the application layer, there can be issues depending on what flavour of IoT is being used, such as say Sigfox, LoRa or one of the cellular methods, such as NB-IoT.
Eric Heiser, head of strategic partnerships at u-blox, sees a particular problem with Sigfox due to it being designed for very small amounts of data being transmitted and the problems with doing over-the-air updates.
“You can’t do over-the-air updates,” he said. However, Gilles Bolumar, security director at Sigfox, said the small data flow was an advantage.
“Because you can only send a small amount of data, it is difficult to use it for other means,” he said. “We also have a lot of protection in our cloud network to detect any change in behaviour for any component, and this can suspend activity or raise an alert.”
With LoRa, Heiser said this was more vulnerable to attacks on the network side. And Bolumar said the way LoRa was made up of private networks increased its vulnerability.
“Each operator has their own LoRa network,” he said. “That can be a risk as it may not be properly configured. With Sigfox, we have a worldwide network and all the configuration and security aspects are the same. With LoRa, each network could be configured differently, so there could be some risk.”
For cellular, Heiser said these benefitted from rules and regulations have been built up over decades. “The security is built into the standards,” he said. However, Bolumar points out that the mass-market nature of devices that could be connected to an NB-IoT network increases the risk of a large number of devices being attacked or used for an attack.
Schieli sees risks in all of them. He said: “LoRa, Sigfox and NB-IoT are all narrow band and it makes it more difficult to implement strict cryptography as you don’t have the bandwidth. It is more difficult to achieve security on these protocols because you need safe mechanisms for sharing a key.”
WiFi is also a particular problem because of the number of default passwords and insecure networks. These days, people expect public WiFi connections to be automatic or at least very quick and simple. That is not compatible with high security.
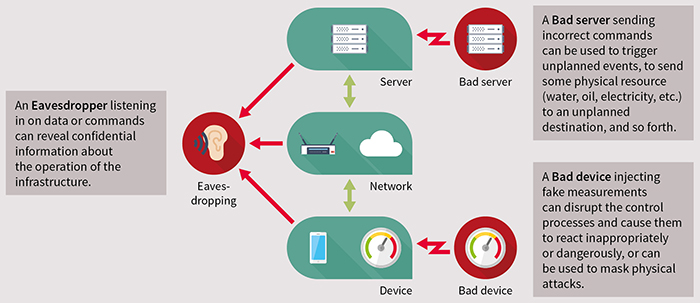
Above: IoT security threats (Picture: Infineon)
The business case for IoT security
Hanna believes it is important to put forward a business case to convince those holding the purse strings that it is worth investing in IoT security. “If you get IoT security right, you are protecting the three things businesses care about most – reliability, safety and profit. If you get it wrong, you impact on all three of these.”
Good reliability increases up-time, improves customer satisfaction and reduces support cost. Promoting safety reduces risk, protects private data and avoids damage to the brand. “If you have a safety event, people stop buying your product,” said Heiser.
Combined, these impact profit and they can help maintain a steady revenue stream, help create new business models and let a company differentiate itself from the competition. “There is a bottom line impact on getting it right or wrong,” said Hanna.
Conclusion
There is no such thing as a totally secure connected system. Being connected creates a route into a device or network that can be used for undesirable purposes. With the growth of the IoT, this problem is spreading to billions of devices. What is clear is that the onus cannot be put on the end user to implement security and some manufacturers are willing to ignore security to cut costs. Therefore, the answer will probably lie in enforceable standards and regulations.










