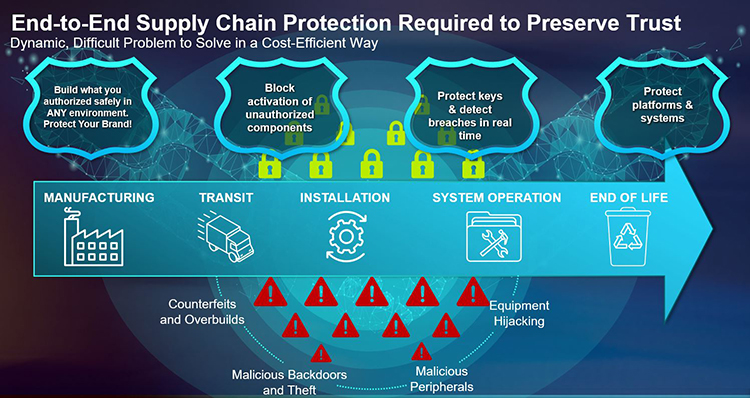
Delivering end-to-end supply chain protection
Lattice Semiconductor Corporation has launched the Lattice Sentry solutions stack and the Lattice SupplyGuard supply chain protection service. The Sentry stack is a combination of customisable embedded software, reference designs, IP, and development tools to accelerate the implementation of secure systems compliant with NIST Platform Firmware Resiliency (PFR) Guidelines (NIST SP-800-193).
The Lattice SupplyGuard service extends the system protection provided by the Sentry stack throughout today’s challenging and rapidly changing supply chain by delivering factory-locked devices to protect them from attacks like cloning and malware insertion and enables secure device ownership transfer. These hardware security solutions are increasingly important to a range of applications, including communications, data centre, industrial, automotive, aerospace, and client computing.
According to Patrick Moorhead, President and Founder of Moor Insights & Strategy: “5G, Edge computing, and IoT are accelerating the pace at which devices are becoming connected, and security concerns are on the rise among high-tech OEMs serving every market. Developers need to know their hardware platforms are secured against cyber attack and IP theft. They need security solutions that support comprehensive protection throughout a product’s entire operating life in the field, which means the solution must be able to dynamically adapt to an evolving threat landscape.”
Deepak Boppana, Sr. Director, Segments and Solutions Marketing, Lattice, explained that attackers are increasingly turning their attention to the firmware layer, as software layers, OS and network level security is getting better every year. So, the firmware/hardware level attacks are a new focus for a lot of hackers. Indeed, according to a 2019 Gatner report, by 2022, 70% of organisations that do not have a firmware upgrade plan in place will be breached due to a firmware vulnerability.
“Lattice continues to execute to our solutions stack roadmap and strategy to provide our customers with easy to use, system-level solutions for key focus applications. The Lattice Sentry solutions stack makes it easy for customers to implement a hardware Root-of-Trust (RoT)-based PFR solution compliant with the NIST SP-800-193 guidelines,” said Boppana. “With Sentry’s validated IPs, pre-verified reference designs, and hardware demos, developers can quickly customise the PFR solution by modifying the C code provided with the RISC-V and Propel design environment to cut time-to-market from ten months to just six weeks.”
The security paradigm is changing, and firmware is an increasingly popular attack vector. The National Vulnerability Database reported that between 2016 and 2019 the number of firmware vulnerabilities grew over 700%. Protecting systems against unauthorised firmware access requires dynamic, persistent, real-time hardware platform security for all connected devices. This includes securing component firmware from unauthorised access and enabling the system to automatically protect, detect, and recover from an attack in an instant.
Boppana added that firmware can apply early on in a system’s operation, right as things are booting up, and sometimes even before that, when the system is being manufactured or is in transit. In addition the COVID crisis is not helping with huge shutdowns and lockdowns worldwide making supply chains even more vulnerable from a physical security standpoint.
Key features of the Lattice Sentry solutions stack include:
- Hardware security capabilities – the Sentry solutions stack provides a pre-verified, NIST-compliant PFR implementation that enforces strict, real-time access controls to all system firmware during and after system boot. If corrupt firmware is detected, Sentry can automatically rollback to a previously known good state version of the firmware so secure system operation continues without interruption.
- Compliance with latest NIST SP-800-193 standard and CAVP certifications – the stack enables implementation of a hardware RoT through its support for the cryptgraphically-sound Lattice MachXO3D family of FPGAs.
- Ease of use – developers can drag-and-drop Sentry’s validated IPs and modify the included RISC-V C reference code in the Lattice Propel design environment without any prior FPGA experience.
- Rapid time-to-market – the Sentry stack provides pre-verified and tested application demos, reference designs, and development boards that can slash development times for PFR applications from ten months to just six weeks.
- Flexible, platform-agnostic security solution – Sentry offers comprehensive, real-time PFR support for firmware and programmable peripherals. It can act as a RoT in a system and/or complement any existing BMC/MCU/TPM-based architecture for full NIST SP-800-193 compliance.
“To provide them with peace of mind in a constantly changing and increasingly risky supply chain environment, Lattice developed our SupplyGuard service to help our customers securely provision their devices while lowering their overall costs,” said Eric Sivertson, Vice President of Security Business, Lattice. “NIST is looking at what’s evolving in the threat space. And we're really moving into what we like to consider a more dynamic environment, and we can solve the problem of PFR platform firmware resiliency. And that gives you protect, detect and recovery in real-time systems.
“So this is really where the Sentry stack shines on Lattice FPGAs. By using Sentry stack on our parts we can, in real-time, watch the memory interfaces onto those parts, and we can detect an attack when it's happening in real-time, as well as authenticate that firmware before we allow it to get loaded into any devices. We like to say that it’s ‘secure the moment it's on’.”
Compared to alternative solutions Sivertson added that TPMs (Trusted Platform Module), are an old technology, and more of a static solution. While it offers a hardware Root of Trust, there's no real-time capability and so their ability to concurrently look at multiple threats on multiple parts doesn't exist.
He continued: “When it comes to secured microcontrollers, you’re going to find mostly the same class of product. They’re going to be a single core von Neumann machine, and so are instruction rather than task optimised. So to monitor multiple factors you’re going to use many clocks and you’re going to configure them in a round robin fashion. So these existing technologies are really not sufficient to deal with these new problems.
“FPGA’s are inherently parallel, so you can run as many instances as you need in order to cover all the products that you want to protect - we can now be called fast optimised, and you can get down to one clock cycle to run multiple tasks on multiple processes.”
Security philosophy
Sivertson delved deeper into the company ethos behind the launch of the SupplyGuard supply chain protection service, stating: “Most silicon vendors today give you a piece of silicon and they walk away, and that's the end of the story. We decided that this process is bigger than that, and if we're going to offer security, we need to be able to be with you throughout the device lifecycle.”
He explained that a part is protected from the minute it leaves the Lattice factory, until the product that's utilising it reaches its end of life - stopping counterfeits and over builds, all the vectors from malicious backdoors, and the hijacking of IP equipment. “We see this as a novel solution, and no other vendors that we have seen are able to do exactly what we do. This is a real trailblazing service,” he added.
With SupplyGuard Lattice is locking the parts. So all the ports that enable you to go to the flash memory to program in the bitstream or the instructions can be locked in such a way that you cannot read what's inside, erase it, or rewrite it.
Sivertson added: “We separate a cryptographic unlock key from those parts. So the minute they leave our factory if you don't have the unlock key, you literally have a bricked part - it'll boot up, it'll start, it'll run, but you can’t do anything with it without the unlock key.
“It's highly resilient to any type of attack throughout the supply chain, as it goes through to the manufacturing site at a customer's manufacturing facility or a contract manufacturing facility.
“This allows us to do what we call ‘secure ownership transfer’. With SupplyGuard, Lattice effectively owns the IP in the part until it gets to the manufacturing point. And that unlock key is what's used in order to change the ownership and put in the new IP that the customer wants. So we give that unlock key to the customer’s part separate from the supply chain and separate from the manufacturing process. The customer then uses that unlock key in order to encrypt their bitstream and secure manifests that they want to put into the product at the manufacturing site.
“By doing this, you don't have to put what we traditionally call, ‘guns, guards and gates’ around your manufacturing facility. You can use the lowest cost manufacturing facility without compromising security. And this is what's very unique to SupplyGuard versus any competitors or vendors that we've seen.
“We’ve dropped the cost while keeping the security very high. And that’s in essence what the SupplyGuard service provides. It’s very novel, unique and it fits well with Lattice’s philosophy of being able to do very high-volume manufacturing at very low cost.”
Key features of the Lattice SupplyGuard supply chain protection service include:
- Robust security throughout device lifecycle – SupplyGuard is a subscribed service that offers OEMs and ODMs peace of mind by tracking locked Lattice FPGAs through their entire lifecycle, from the point of manufacture, through transport through the global supply chain, system integration and assembly, initial configuration, and deployment. SupplyGuard helps protect OEMs by:
- Ensuring only authorised manufacturers can build an OEM’s design, regardless of their location.
- Providing OEMs with a secure key infrastructure to prevent the activation of their IP on unauthorised components to stop product cloning and overbuilding.
- Securing devices against the download and installation of Trojans, malware, or other unauthorised software to protect platforms and systems against equipment hijacking or other cyberattacks.
- Flexible, low-cost implementation – SupplyGuard is highly customisable to meet the specific security and supply chain needs of OEMs in every industry Lattice serves. The service lowers the operating costs associated with implementing a secure manufacturing ecosystem.











