Memory chips can help secure and manage IoT devices
There’s a growing appreciation hardware security is the essential foundation of IoT device and network security. IoT devices, most of which are sensors, actuators, or human-machine interfaces, have semiconductors at their heart. Most commonly, these are microcontrollers (MCUs) or application-specific integrated circuits (ASICs), so there’s been a lot of work in recent years to figure out how these chips can be designed and configured to support device security. Chris Jones, Crypto Quantique’s IoT security specialist discusses.
The solution is to make a semiconductor chip’s identity a binary number, typically 128 bits long. Cryptographic keys are used to encrypt data sent over IoT networks and these consist of strings of random numbers. In both cases, the more random the numbers, the harder they are to guess and the harder it is to hack into the chip, or into the IoT device that it drives. (You can learn about random numbers here).
Most of the time, the binary numbers for identities and cryptographic keys are ‘injected’ into the memories of MCUs or ASICs, where they are stored until needed. This key injection is part of a procedure that uses a hardware security module (HSM), which is a special kind of secure computer incorporating a random number generator (RNG).
Because injecting and storing keys involves some risk – both the process and the storage medium need to be protected from attack – there has been a growing trend towards generating random numbers within the fabric of the silicon by exploiting a phenomenon known as Physical Unclonable Functions (PUFs).
PUFs may be derived from inherent random physical properties within the structure of silicon wafers during chip manufacturing. For example, the microscopic ‘roughness’ of the oxide layer of a CMOS wafter is the result of random variations in the thickness of that layer. This creates the opportunity to derive random numbers from random physical characteristics. Academic papers have cited over 40 different types of PUF, but few are yet in use, and many will never be commercially viable.
In practice, PUFs do not always produce enough random numbers to satisfy the needs of connected devices. Several may be needed to enable secure IoT device connectivity to a range of services and applications. Sometimes, the PUF will be used to create a unique, immutable, and unclonable device identity, and it will be complemented by key injection for cryptographic keys. PUFs can also be used as a 'wrapper' for cryptographic keys to prevent them from being read by malicious actors. In other words, they can be used to encrypt the encryption keys.
While the current choice of MCUs that employ robust PUFs is limited, designers of IoT devices should not overlook the opportunity for using secure memory chips to provide security. Flash memory is typically used with microprocessor-based systems, where embedded memory is not available. However, it can also be used with any MCU, typically via a QSPI interface, avoiding the need for engineers to move away from the MCU ecosystems with which they’re familiar.
One PUF-based memory family, ArmorFlash NOR Flash from Macronix, has the added advantage of being compatible with a software platform that enables provisioning, onboarding, and lifetime management of IoT devices at scale.
ArmorFlash serial NOR Flash as the foundation of IoT device security
The security of ArmorFlash is PUF-based. According to Macronix, ArmorFlash is designed to deliver data privacy and protection for automotive and industrial applications. The memories enable secure identification and authentication, data encryption and decryption, including AES 256-bit encryption, and easy interfacing to other system components via standard SPI, QSPI, and OctaBus interfaces.
The Flash PUF gives each device a unique and immutable fingerprint, with high entropy (randomness) that cannot be predicted or cloned.
The technology has been subjected to independent scrutiny but standards organisations too.
The ArmorFlash MX75 series is PSA Certified Level 1, which means that it has undergone an independent, lab-based assessment to ensure that it meets security best practice. And the National Institute of Standards and Technology (NIST) in the US has evaluated and certified the cryptographic algorithms for ArmorFlash.
In short, ArmorFlash is a secure memory for data and code that can also serve as a hardware Root-of-Trust for an IoT device by providing a unique ID, authentication, and encrypted links.
Connecting from chip to cloud (or on-premises server)
Of course, having a memory-based, secure Root-of-Trust embedded within an IoT sensor or actuator, is only the starting foundation for an IoT. The next steps are to securely provision these devices with firmware so that they carry out their intended purpose, securely connect them to services and applications hosted on servers (usually in the cloud but sometimes on-premises), and then manage them throughout their operating lives. Many IoT devices have a life expectancy of 10 years, and some are designed to function for 25 years or more. During that time, security can only be maintained with regular firmware updates and when the devices are no longer needed, they need to be decommissioned so that they don’t present a forgotten window through which hackers can access IoT networks.
To enable its customers to do this with ArmorFlash, Macronix adopted Crypto Quantique’s QuarkLink chip-to-cloud software platform. The combined technologies can be deployed without specialist cryptographic knowledge and at scale, enabling thousands of IoT devices to be connected to services and applications within a few minutes. Figure 1 summarises the process.
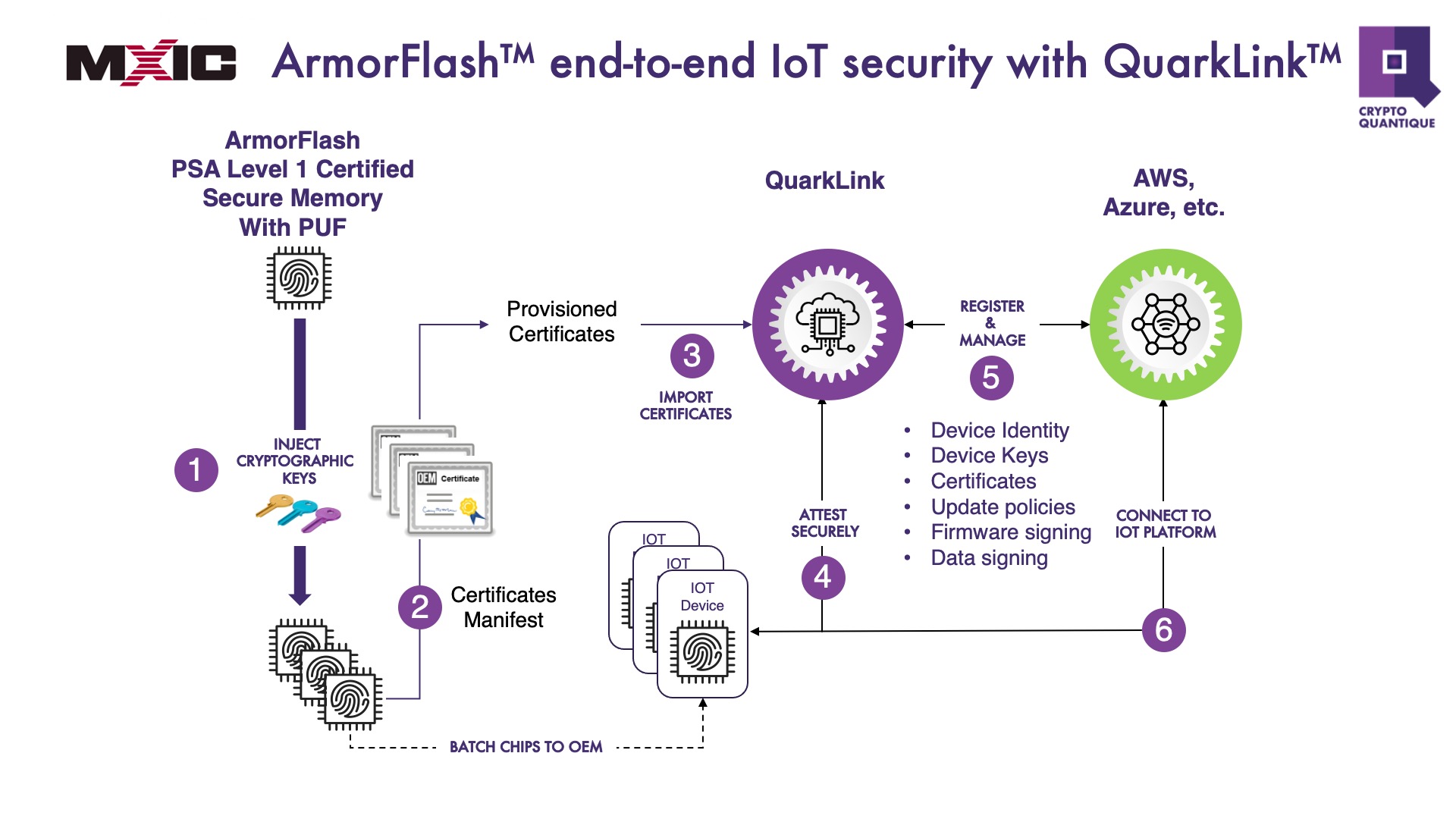
Figure 1: With Flash memory as the Root-of-Trust, a single platform can be used to deploy IoT networks securely at scale
How the QuarkLink user platform works with ArmorFlash
The QuarkLink platform has a simple graphical user interface (Figure 2) that is used to provision, onboard, and manage the IoT devices that use ArmorFlash as a Root-of-Trust.
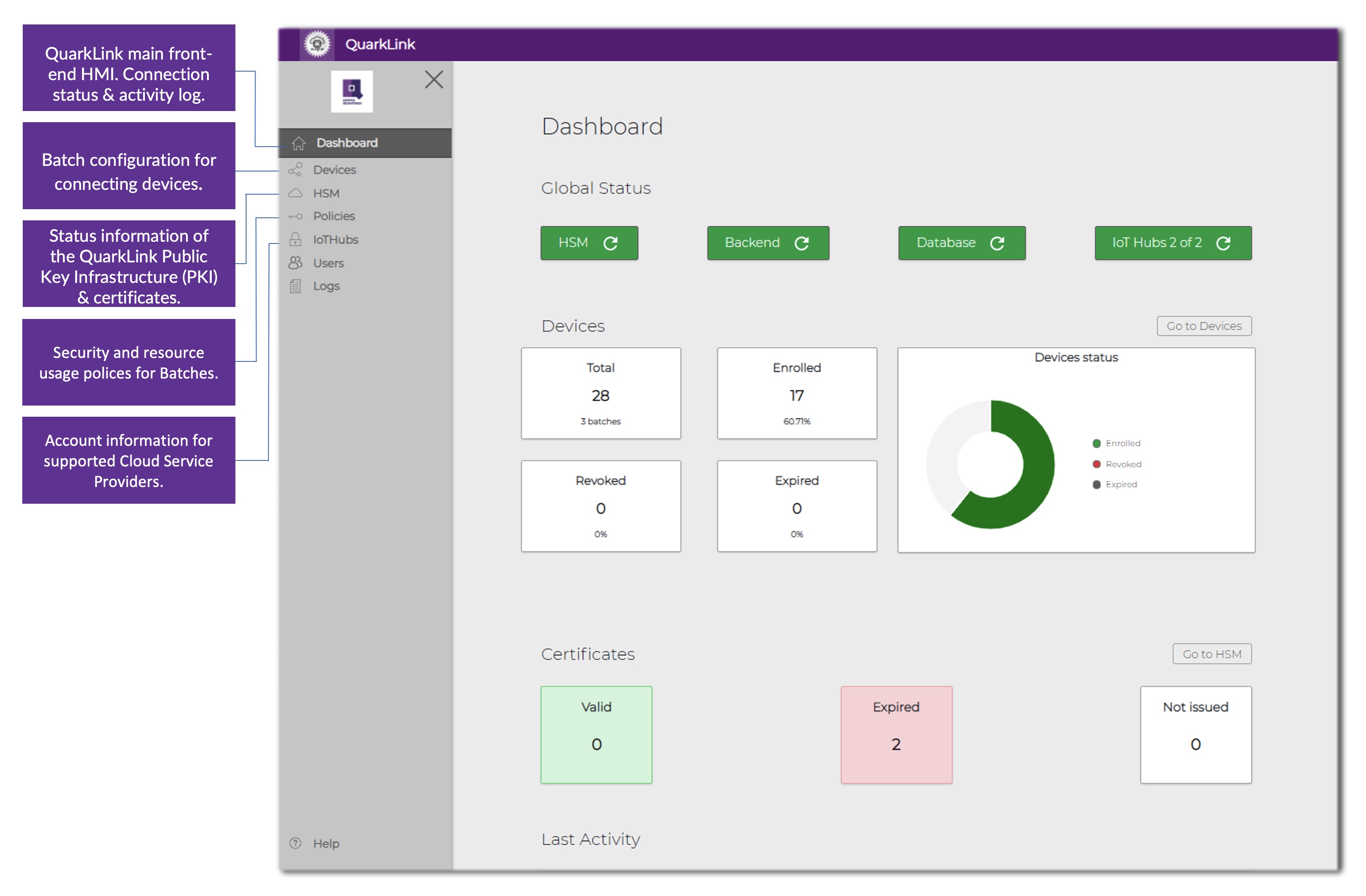
Figure 2: Via this simple interface, the complexities of device provisioning, onboarding, and lifetime management are reduced to a few key clicks
This step-by-step process is implemented through a simple graphical user interface:
1. Chip identities are registered on the QuarkLink platform.
2. The pre-defined server policy is chosen from a drop-down menu. It's usually AWS, Azure, or Mosquito but QuarkLink can be adapted for others.
3. A batch of chip identities, based on the public key of their security certificates, is uploaded and checked against those registered on the platform.
4. For a device to onboard, it makes a request to QuarkLink which sets up a secure communications link using the industry-standard Transport Layer Security (TLS) protocol. Through this secure link, the devices are asked to prove their identities.
5. With that done, securely encrypted connections are established then the devices communicate with the server-hosted applications.
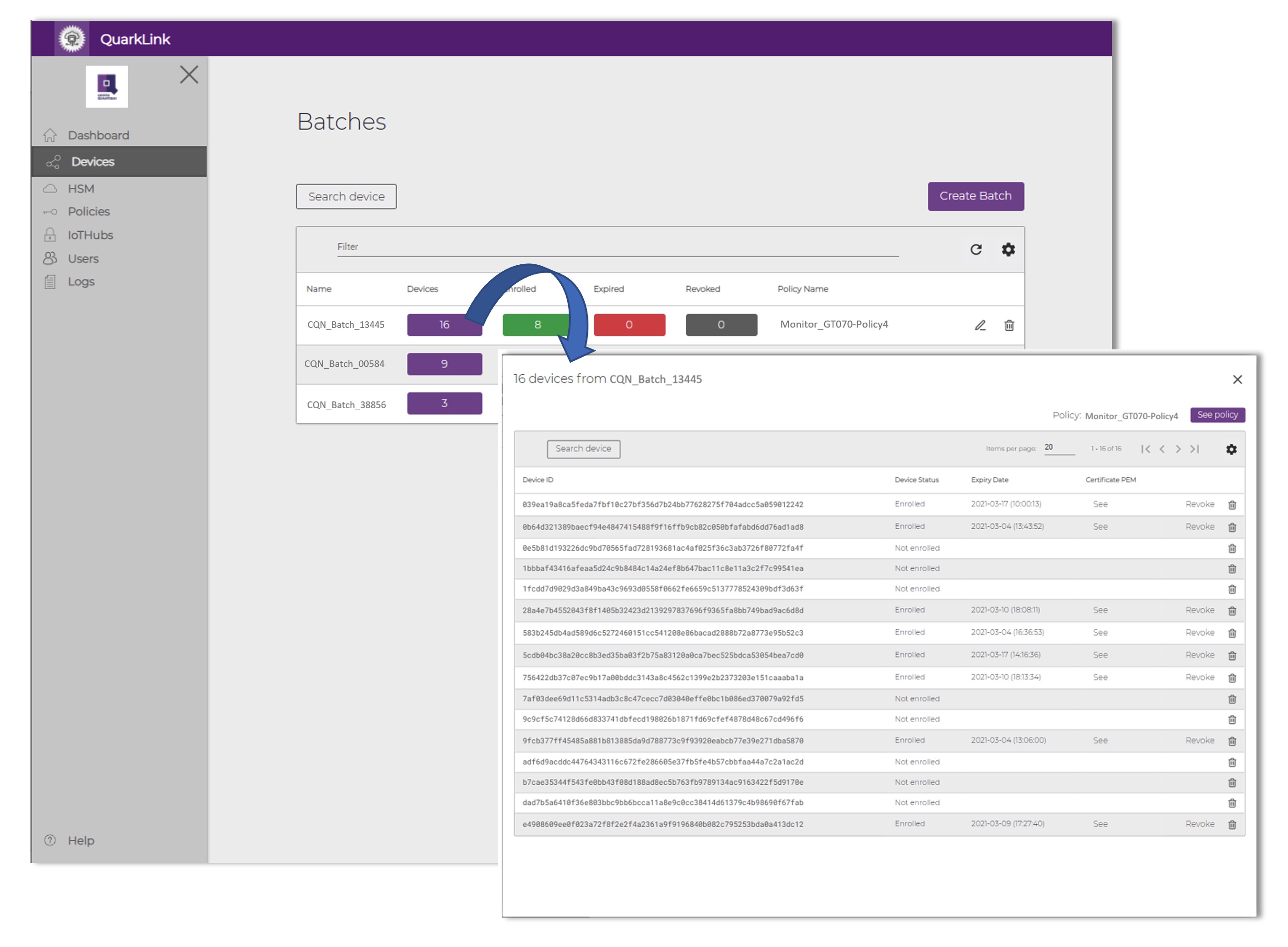
Figure 3: Using batch processing, thousands of IoT devices can be securely onboarded to server applications simultaneously within minutes, using just a few keystrokes
This QuarkLink platform makes it easy to manage ArmorFlash-based security throughout the operating life of IoT devices. It manages certificates and security policies, facilitates firmware signing and encryption for secure over-the-air (OTA) updates, and manages key and certificate renewal. Certificate renewal is sometimes needed after a system fault or external interruption. Devices can be disconnected from the network if they fail, or their security is breached. Onboarding can be repeated if the owner of the device owner is changed.
With the right platform, using secure memory simplifies IoT security
Implementing a secure IoT network can take months and many projects fail. The inability to provide economical yet comprehensive IoT device security is one of the main reasons for failure and it is preventing many enterprises from realising the promised benefits that the IoT can bring, particularly in industrial applications. Ecosystems such as the one described here, that combine proven Root-of-Trust technologies in NOR Flash with a comprehensive, secure software platform, promise to eliminate many of the challenges to successful IoT deployment.






