The complex nature of IoT devices and cyber security
The simplest definition of the Internet of Things (IoT) is that it is a giant network of connected things (application, devices, and people). Information sharing and data flow between things are at the core of this technology. IoT describes the domain where just about everything can be connected and communicated with in a smart manner.
The Internet of Things allows objects and entities to be sensed and controlled remotely across existing network infrastructure, creating opportunities for integration between the physical world and the smart systems, resulting in improved efficiency, accuracy, and economic benefit.
Today, people across the world are heavily dependent on IoT, which is touching every facet of our lives. The various application areas for IoT include wearables, smart retail, smart home, connected health, etc. All of these things need to be tested and validated to ensure the quality and the accuracy of the associated data. Quality assurance in IoT thus refers to the validation process of various aspects associated with communication, computing, and, of course, the software, which remains an integral part of IoT.
According to Gartner, the Internet of Things base will grow to approximately 26 billion units by 2020. Based on TMT predictions in 2015 by Deloitte, IoT and corresponding connectivity revenues are growing at about 10-20% annually, while the apps, analytics, and services are increasing even more rapidly, at 40-50%. But very few parameters exist to check and ensure the quality of these IoT-enabled devices and machines from a quality and security perspective. The following sections will provide a comprehensive analysis of approach and methodologies that can be used for securing and testing IoT-enabled devices and the various challenges and complexities involved when compared with the traditional approach.
According to Gartner, IoT product and service suppliers will generate incremental revenue pg more than $300bn, generally in services, in 2020. It will result in $1.9tn in global economic value added through sales into diverse end markets. Creating a robust and reliable IoT system thus becomes an important point of focus, with an approach to test the IoT-enabled systems and people focusing on applications and devices.
Internet of Things (IoT)
IoT has been the most pertinent word in the technology space and the engineering circles over the past few years. With increasing demand for cutting edge devices such as smartphones, tablets, electric cars, and wearable devices, the Internet of Things is most likely to transform and shape the technology ecosystem with many more devices going to be ready for this technology in the coming years.
The concept of this technology is very simple: Connect all things to the Internet. The 'things' here may refer to computer-based smart devices with sensor and network communication functionality, which includes devices such as smartphones, webcams, microphones, medical diagnostics devices, smart watches, and even vacuum-cleaning robots. IoT requires smart elements or units to make it running. An IoT unit is any device or system that is used for communication between systems and devices through the internet. “The Internet of Things is the network of physical objects that contain embedded technology to communicate and sense or interact with their internal states or the external environment,” in Gartner’s definition.
IDC estimates that, toward the end of 2013, there were 9.1 billion IoT units installed. It expects the installed base of IoT units to grow exponentially at 17.5% CAGR over the forecast period to 28.1 billion in 2020. As per the IDC market report, the IOT market will grow from approx. $655.8bn in 2014 to a humungous $1.7tn in 2020, with a Compound Annual Growth Rate (CAGR) of 16.9%.
IoT has made great progress in the technology market of wearable devices. There is a recent trend toward people getting smart watches, health bands, and eyewear and using them in tandem to for health and fitness purposes. There are serious talks of wide usage of smart attires and body-embedded technologies as well. All this will be connected through the Internet, to give a boost to the IoT technology.
Assessing embedded and Internet of Things devices
There is a strong need for the traditional software quality assurance and security models to evolve along with IoT. Quality assurance and security teams should start focusing more on usability testing, simulating the environment where the devices will be used, making sure information is exchanged in a secure manner and that the performance of these devices are not affected. Today, the IOT space mainly comprises the mobile and embedded systems. Thus, the general test approach for testing has to be significantly different from the traditional way of testing desktop or Web applications.
The quality assurance and security teams must create use cases and test scenarios that go beyond the use of mouse and keyboard to interact with these embedded devices They should take into account the body movements, voice commands, and touch and sensors utilisation while designing the tests and, at the same time, they should focus more on the usability and performance aspects of these devices. The key for quality assurance and security teams to achieve quality testing is to think about the way the user interacts with mobile or embedded IOT devices. Since all of these devices actually function with us, testing how the user experiences these devices becomes imperative. If we do not test the user interaction, our assessments and decisions of quality will be lacking some of the most important information needed to determine whether or not the devices are ready to be catered securely to the customer. Why is user experience testing so important to IOT devices?
In general, testing should include all things physical, including sizes, shapes, and genders of the users. It should also include testing all sensory reactions including sight, sound, and touch, along with orientation, or the interaction with human movement. All these are incredibly crucial parts of the test. Finally, we must consider the value and most thoroughly test in terms of the user’s perceptions, mindsets, biases, and emotions when interacting with the IOT devices.
The first step towards adopting the user experience approach is to understand the end user’s/customer’s requirements. When testing a new device, one can observe contributors using the corresponding device in prototype lab. In this setting, they can observe and focus on their reactions and possibly discuss with them their feedback and responses to the device. Thus, the key to following a test approach for user experience testing involves not only 'field' testing but also testing in the real environment in which the customer is present.
Below are some of the test scenarios that could be created as part of IOT testing and security:
- Verify that a device can register with a network and the data connection is made successfully.
- Verify that all the devices involved in the IoT testing can register with the network.
- Verify that, devices involved in the IoT testing can transmit and receive data through the network.
- Verify that only IoT devices with appropriate authentication and authorisation can connect to the network.
- Verify that IoT devices successfully disconnect from the network when the user asks them to.
- Verify that, devices involved in IoT do not frequently disconnect from the network until the user specifically asks them to.
- Verify that, if a maximum number of connections (as per the requirement) is attained, the IoT device stops any attempt to link to the network for a predefined duration.
- Verify that, in the event that data volume surpasses what is defined in the requirement, the IoT device should not initiate any more transfer of data for a predefined duration.
- Verify that IoT device can transfer data in low power mode.
- Verify threshold signal range for an IoT device and how far the device can operate from the network.
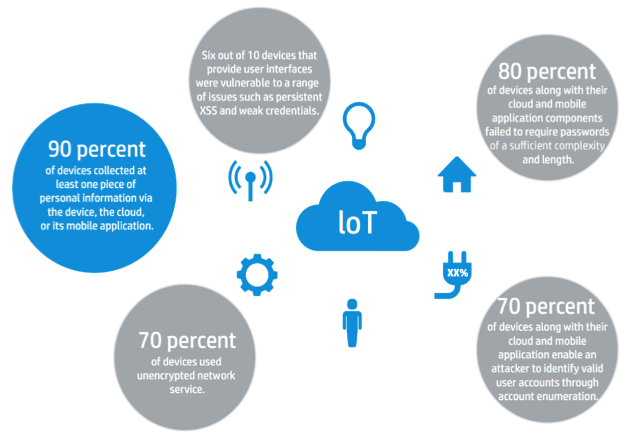
Figure 1
Figure 1 shows that IoT, as of now, is highly vulnerable and is not a foolproof system. An aggressive approach to IoT testing by building a framework and executing different types of testing can only help in making the ecosystem robust.
Although it is one of the most critical areas in testing IoT apps and services, security testing is often overlooked due to market pressure on companies to launch new products/releases. Also, there is at times a lack of understanding security testing by the IoT manufacturers. Needless to say, security testing is very critical and cannot be missed, as the device’s behavior affects the end user’s everyday life and the device can actually be configured through a wireless connection, remotely. So one can imagine how vulnerable these devices become if these devices are wrongly configured intentionally! As an example, taking control of an IoT system of another user by cutting off its transmission can be done by an IoT system remotely. Thus, security testing must assure that the system is accessed only by an authorised user and the information exchanged between the device and the system is not intercepted and modified by a hacking attack. A few security features that can be included as part of security testing in an IoT ecosystem are insufficient authentication/authorisation, insecure network services, privacy concerns, insecure software/firmware, lack of transport encryption, etc.
Complexities involved
Nowadays there are many applications that can expand the existing connected systems. However, different organisations need to perform appropriate testing on the IoT applications before they go live, get connected, and start transferring data. The role of quality assurance and security is therefore very important, because it involves testing the hardware and software and sending to and fro huge amounts of real-time intelligence. The main challenges and solutions that quality assurance and security managers have faced include:
- Integration of the hardware and software in IoT: The IoT ecosystem is made up of devices, sensors and applications. As testing evolves and becomes as important as development, there is a shift in the focus from just testing the applications in a particular defined environment to testing the experience in a dynamic, changing environment. With several million sensors and different types of devices that provide the experience in conjunction with intelligent software, merely validating the functionality is not sufficient in an environment as complex as IoT.
- Just a normal working system is not the benchmark: The current set of intelligent programs ensures that a working set of device software is not enough to certify an IoT system or service. For instance, a shipment tracking system with sensors and devices that communicate with multiple software backends will need smart algorithms to ensure correct product delivery. This requires a very robust quality assurance and security validation process. The use cases are extremely complex in real time; the variety of real-time scenarios can become a challenge for quality assurance and security.
- There is an ever-increasing number of communication sensors. To create an environment to test a real-time IOT applications implementation is a challenge that includes not only configuring an environment to validate the correctness but also to assess scalability and reliability. The IOT system is built on many analytics engines and demands substantial practice and understanding in simulation to build out a test environment. Hardware and the protocols are always well tested by makers of the device; understanding the application intelligence and device’s real-time complexity is an extremely complex science and new art for many application developers and quality assurance and security experts.
The common security observation
Across industry, the following observations relate to people, processes, or technology that are the most common root cause for lack of security in IOT:
- There is no clear ownership of device security. Though the product R&D teams are knowledgeable regarding the product design and configurations, they don’t perceive themselves as being accountable for owning security requirements and proactively embedding security into product design, development, and deployment lifecycle.
- There are no baseline security requirements for product R&D teams to use. For certain products, the product R&D teams are more aware of technical security capabilities, especially when these products become more accessible remotely. For others, there is more reliance on physical security controls of the hospital or clinical environment where devices reside.
- In general, the process is lacking in:
- Applying security into product development lifecycle, including lack of a formal security risk assessment
- Raising awareness of device users (e.g., calling out specific security responsibilities for hospital users to adhere to via user manuals, training, standard end user license agreements, etc.)
- Managing security for those products that are outsourced to third parties for design and development
- A formalised security patch management process
- There is a lack of basic security controls for most of the in-scope devices. The lack of these security capabilities (such as unique user account and password controls, anti-virus, security patching, logging and monitoring, etc.) introduces increased risk exposure, especially as these devices are moving online or becoming remotely accessible. Even for devices that are only connected to the local hospital network, the increasing threats of computer virus contamination or hacking activities (against the hospital environment) potentially make these devices more vulnerable and render physical security controls less effective.
- A lack of technical security control capabilities in devices is beginning to impact device sales. The use of legacy versions of Windows operating systems, the inability of customers to patch operating system vulnerabilities, and difficulties in implementing anti-virus capabilities on the devices has led customers to not select a firm’s devices, or require them to go to extra efforts (e.g., use of network isolation) to utilise their devices. They can also lead to regulatory compliance challenges due to the increased security risk exposure (e.g., unauthorised disclosure or loss of patient information etc).
In a nutshell, IoT security and testing complexities go beyond devices and sensors to include the added complexity that comes with a big volume of data transaction and communication (i.e., huge volume, velocity and variety), which makes testing of real-time IoT certification a major headache.










