Providing protection for the 'Internet of Tiny Things'
Even devices with minimal processing resources can now implement Internet access, which makes securing these resource constrained devices a challenging necessity. By Alan Grau, David West, Icon Labs.
Devices such as sensing and control units in industrial environments, utility meters, lighting control systems and smart home devices make up a large portion of the IoT that we refer to as the 'Internet of Tiny Things'. As their numbers skyrocket, so has the number of cyber-attacks targeting these devices. Despite the growing threat from hackers, few devices include robust, multi-layered security to protect against attacks. This is particularly true in the most resource constrained devices.
The embedded marketplace needs a resource-friendly security solution designed to provide protection against Internet-based attacks. Embedded firewalls provide an ideal solution. The firewall is integrated directly into the communication stack at the link layer of the supported protocol and configured with a set of rules specifying what communication is allowed. For TCP/IP, those rules block packets by IP address, port, protocol, and other criteria. The integrated firewall ('embedded firewall') provides a basic, but critical level of security by controlling what packets or messages are processed. Because each packet or message is filtered before passing from the protocol stack to the application, many attacks are blocked before a connection is even established. The result is an effective layer of protection with minimal impact on system resources.
An embedded firewall enforces a set of rules or policies that govern who the device can talk to, what protocols and ports can be used, and who can initiate communication with the device. Embedded devices typically have very well defined communication requirements, only supporting a small number of protocols and ports and in many cases only communicating with a limited number of devices/IP addresses. Some embedded devices need the ability to communicate with any IP address, but even then communication is usually limited to a few protocols and ports that are open to the world.
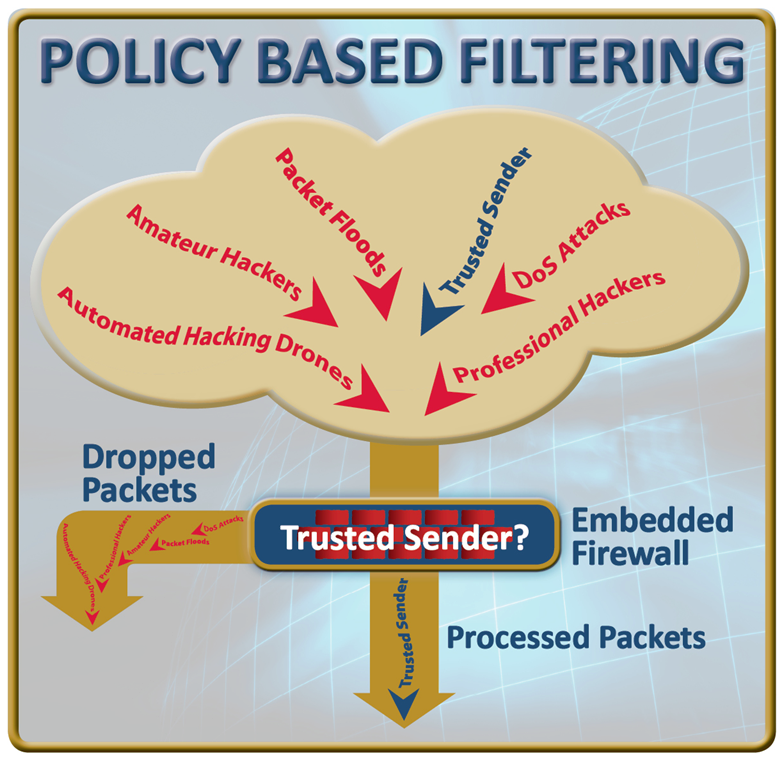
These well-defined communication requirements allow the creation of restrictive firewall policies. The firewall enforces policies by filtering packets as they are received, comparing each packet to the policies and blocking anything not matching the communication policies.
By only allowing packets meeting communication policies, most cyber-attacks are blocked. A hacker attempting to login to the device is blocked because their IP address is unauthorised. DoS attacks and many other cyber-attacks will also be blocked because they use ports or protocols blocked by the firewall or because they originate from an IP address not allowed by the policies. When combined with password authentication, this creates an effective, resource-friendly defence against cyber-attacks.
Intrusion detection
Devices without a firewall or other security capability provide an easy target for hackers. A hacker can probe these devices for weakness, or run dictionary attacks against these devices with no risk of detection. A hacker can run a brute-force dictionary attack against an embedded device for weeks on end, attempting thousands and thousands of login attempts and no one would ever know. With an embedded firewall, the device can report failed authentication attempts, firewall policy violations and device specific events to a management system. This information allows detection and mitigation of attacks, providing a critical and missing line of defence for these tiny devices.
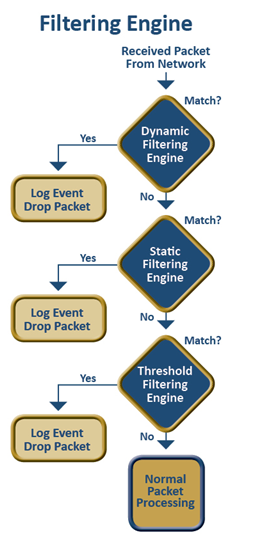
The firewall filters packets as they are received, blocking unwanted packets, unfriendly login attempts, and DoS attacks before authentication is allowed to begin. One or more methods are implemented by the filtering engine to enforce firewall policies and block Internet-based attacks. Common filtering methods are Static, Dynamic and Threshold-based filtering. The firewall depends on properly defined policies allowing required communication and blocking all other communication. Defining the embedded device's communication requirements is the first step. Once the communication requirements are specified, they are coded as a set of rules. The rules specify the IP addresses, ports, and protocols used by the device to communicate with other network nodes.
For some devices the communication requirements are very well defined and restricted. Other devices require broader communication capabilities, resulting in a broader, but not necessarily less secure, firewall rules.
All packets received by the device are passed to the firewall for filtering and compared to the firewall rules. Packets not matching the firewall rules are dropped. As a result, attempts to hack into the device are blocked before a connection is even established. Icon Labs provides a solution to the problems and constraints of implementing security for resource constrained devices. Icon Labs' Floodgate firewall is a portable, source code product that can be integrated with an embedded OS or RTOS. Floodgate is designed specifically for use on small footprint devices, from embedded Linux systems to 8-bit MCUs. The firewall controls the packets the embedded system processes and blocks invalid login attempts, denial of service attacks, packet floods, port scans and other common Internet-based threats. Floodgate also provides event reporting and intrusion detection capability, enabling detection and mitigation of threats for even the smallest of devices.










