How to build up your IoT security, confidence and trust
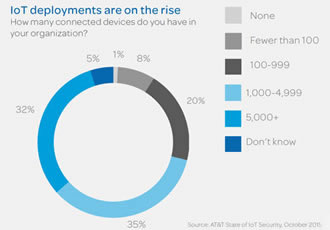
Lack of security confidence is one of the top concerns enterprises have about the Internet of Things (IoT). AT&T’s CEO’s Guide to Securing the Internet of Things, which featured survey results from more than 5,000 enterprises worldwide, found that 85% of enterprises are either in the process of, or planning to, deploy IoT devices.
However, only 10% feel confident they can secure those devices against hackers.
Author: Rodney Elder
These IoT security concerns are not just isolated to businesses; they also plague consumers. Smart, WiFi-connected consumer products such as televisions, phones and wearables are fast becoming a threat to personal privacy. For example, some 'always on' consumer devices can surreptitiously record consumers as they communicate in their homes. This may constitute unlawful surveillance under federal wiretap law, according to the Electronic Privacy Information Center. In addition, many consumers have no idea how much of their personal data is being collected by these devices or how it is being used.
New IoT privacy standards and architectures for deploying IoT infrastructures may help mitigate some security issues. However, the best way to improve IoT security is to have a method to monitor or observe IoT traffic 'on the wire' in real-time and a way to report on-network flow anomalies and status. These can be achieved with an 'IoT audit point'.
An IoT audit point is a foundational building block for establishing trust in an IoT solution. This system sits at the epicentre of IoT interconnections, constantly observing networks for the normal, predictable states that define traffic consistency. When abnormal flows are detected, an IoT audit point would have physically protected links and backend secure connections for transparent reporting.
The components and requirements of an IoT audit point include:
- A platform for network flow and/or wire data observation
- Access to public and private networks
- Interconnection to platforms for data storage and wire data analytics
- Interfaces for scalable, on-demand, real-time anomaly reporting
To ensure the highest level of security, an IoT audit point should be independently operated outside of vertically contained IoT platforms or networks that depend on public Internet transit and transport. This means direct and secure interconnection is vital for a trustworthy IoT audit point.
There are many software solutions available for network/wire data monitoring and capture and analysis, and each address the task in their own way. However, where these tools are deployed in the system and how they interconnect is critical to the applicable function of an IoT audit point. This is where globally distributed IoT audit points with proximity to enterprise IoT interconnection hubs are vital.
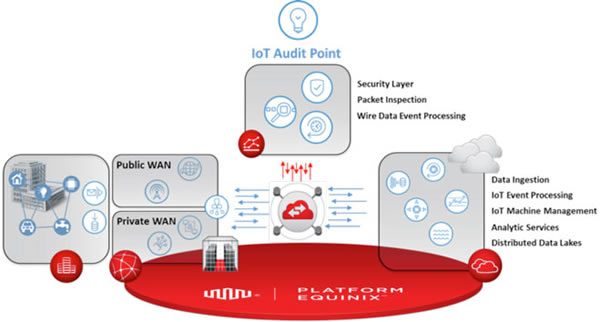
IoT audit points must be placed in physically secure locations (see diagram below) and uniquely positioned for rapid and scalable deployment of network wire data tools with east/west visibility of:
- private and public network-to-cloud
- cloud-to-cloud
- private network-to-partner private network
 Building greater IoT trust
Building greater IoT trust
The Online Trust Alliance (OTA) is well known for its online security initiatives and has expanded its focus to the IoT. Their goal is to develop a security, privacy and sustainability trust framework for IoT devices, potentially with a certification programme. Standards groups and forums such as the IETF, ITU, IEC and the IIC are each working to tackle these issues from their vantage point, and each are contributing components to address the IoT security concerns. However, these components need to be integrated and the final solution must be able to observe 'out of the ordinary' activity.
The standardisation and certification of secure technology implementations may be enough to build confidence, but not enough to instill trust. Trust in IoT can only be gained by reducing security breaks. And the best method for identifying these breaks is to use an IoT audit point to analyse end-to-end network traffic flows, from client to trusted service.
An IoT audit point needs to remain instantaneously and hyper-aware of when anything, other than well-defined network flows, is modified, added to or mis/redirected. These key and fundamental wire data meta profiles are the best leading indicators of anomalies. Correlating and reporting outliers and anomalies within typical network traffic flows by means of a simple scale or binary normal, versus a distressed data flow, is a huge step toward providing transparency and building trust in IoT. In the Gartner report, Use Data- and Analytics-Centric Processes With a Focus on Wire Data to Future-Proof Availability and Performance Management, analysts Vivek Bhalla and Will Cappelli said: “While logs and APIs will still be the dominant data sources, use of wire data will become increasingly important.”
The ability to transparently observe, monitor and report IoT data anomalies and breaches via IoT audit points will be paramount to instill business and consumer security, confidence and trust in the Internet of Things.










