Cybersecurity: The importance of protecting data at rest with VxWorks
Cast your minds back a few months ago, Equifax had a data breach that exposed to hackers the names, social security numbers, credit card numbers, driver’s license numbers, and other sensitive personal information which resulted in a total of 145.5 million consumers impacted by this cyber security breach after the forensic investigation concluded.
Guest blog written by Ka Kay Achacoso.
The resulting outcry from potentially affected businesses and consumers underlines the extremely heavy impact when confidential data gets into the wrong hands. The Equifax incident, along with the growing number of data breach incidents reported, is evidence that data theft is persistent and is growing more sophisticated.
Data breach on the type of devices running the VxWorks real-time operating system (RTOS) can mean exposing passwords into a larger system, or giving away keys to communication codes, or exposing intellectual property that allows rivals to replicate the device’s design.
Protection of device data is important for more than security of a single device. Keeping device data secure is important for the integrity for the bigger system to which the device belongs.
The main attack surfaces for data breaches are either where the data is travelling over the network (data in motion), or where the data is physically stored (data at rest). Both are important to protect. This blog discusses how VxWorks addresses protection of data at rest.
Data Security using VxWorks Disk Encryption
VxWorks provides protection for data at rest with disk encryption that is backed by hardware crypto-processors for hiding passcodes. This hardware-rooted security system allows passcodes to be stored on the device as hardware-encrypted bytes. Only the exact same physical piece of hardware can derive a disk’s decryption key from the passcode files.
If a hacker manages to retrieve the contents of a disk containing sensitive information, either by duplicating the bytes in the disk, or by obtaining the physical memory of the disk, the contents would look like random disorderly bytes that cannot be understood. A decryption key, derived from a passcode, is needed to decrypt the disk into an intelligible form.
If the hacker also manages to obtain the files holding passcode information, that file will also be meaningless. The passcode information can only be decoded by the original hardware. Not even the manufacturer who entered the passcode information in the first place can decode that file without the original hardware.
Figure 1 gives an overview of how the disk encryption and hardware-backed secrets repository works. The hardware crypto-processor contains encryption/decryption keys hidden inside its hardware. The processor can encrypt short data blocks. Once encrypted, the data can only be decrypted into its original form using the same hardware crypto-processor.
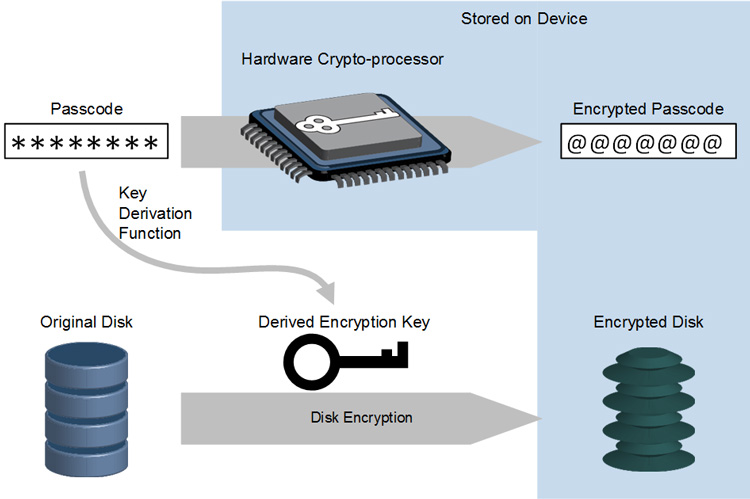
During setup, the entire disk is encrypted with a key derived from a passcode. The hardware crypto-processor encrypts the passcode. The original encryption key and the original passcode are then deleted. Only the hardware-encrypted passcode is kept on the device.
At runtime, once the application provides the correct identification code, the hardware crypto-processor decrypts the passcode to its original form. VxWorks then mounts the disk as a decrypted file system using the key derived from the passcode. As applications access the files for regular file operations like create, remove, read, and write, the disk remains in its encrypted state.
Data Security using Crypto-processor Hardware Support
On Intel Architecture platforms, VxWorks supports the Trusted Platform Module (TPM) technology as the hardware crypto-processor. VxWorks uses the software package tpm2-tss from Intel that implements the Trusted Computing Group Software Stack (TSS) specification to interact with the TPM. More details about TPM support can be referenced in a previous blog about using TPM to seal data here.
The TPM data sealing blog talks about TSS to protect individual files. Protecting data using TPM through the use of VxWorks disk encryption and through the use of TSS API directly protect data using TPM. The advantage of using the VxWorks disk encryption method is that the encryption process is transparent to the application as file operations are performed.
On NXP Power Architecture platforms, VxWorks supports the blob protocol built into NXP security engines on SEC 5.x modules. These security modules are found on certain micro-controllers such as the NXP T1020 and the NXP T2040. The blob protocol encrypts data with a different key every time it is invoked, and that key itself is encrypted by the secret key-encryption key inside the security engine.
Data Protection using Hardcoded Master Key Passwords
For platforms with no hardware security modules, VxWorks can use a hardcoded master-key password that is stored in obfuscated form on the device. In this case, data security relies heavily on the manufacturer’s security processes to keep the password a secret. The obfuscated master-key password serves as a deterrent for attackers from easily accessing the disk encryption passcode. This software-only solution satisfies low-level security requirements, but for higher security levels, a hardware root of trust is recommended.
VxWorks provides a Key-Encrypting Password (KEP) provider framework to enable custom hardware security engines. So if the crypto-processor on your hardware is not listed in the supported list, you should look into using the custom KEP provider framework to ground your disk encryption root of trust to your hardware.
Secrets Repository
The same repository that stores hardware-encrypted disk encryption passcodes is also available for storing other secrets. Applications can store login passwords for other systems, or passcodes for other encryption keys in the secrets repository. The secrets repository ensures that sensitive data that are moved off of the device cannot be understood.
The caveat to using hardware crypto-processors is that if the secret master key is cleared, the loss of data is permanent. No one can recover the original passcodes, and no one can recover the contents of the encrypted disk. For some situations, the loss of data is preferable to data ending up in the wrong hands. Nevertheless, organisations should have strong policies in place around when a device can have its crypto-processor cleared.
Wind River continues to invest in security technologies in its Internet of Things (IoT) solutions.
You can learn more about VxWorks Security Profile here.
Courtesy of Wind River.










