4 ways to secure your Linux-based system
The world is increasingly interconnected and a result of this is the exposure to security vulnerabilities has dramatically increased as well. The intricacies of maintaining today's Linux-based platforms make it very challenging for developers to cover every potential entry point. In 2019 there was an average of more than 45 CVEs logged per day.
Guest blog written by Glenn Seiler.
How does a development organisation keep up with that? In order to stay on top of this, developers must increasingly spend more time and effort integrating Common Vulnerabilities and Exposure (CVE) patches into their solutions, at the cost of spending time developing their applications.
Security attacks come in many forms and use various entry points. Each attack type comes in several flavors, as there is usually more than one way that they can be configured or camouflaged based on the experience, resources, and determination of the hacker. While some threats are more prevalent than others, a developer needs to protect against all vulnerabilities. The following chart shows the increase in CVEs over the last 6 years, and how many of those CVEs actually impact any given distribution.
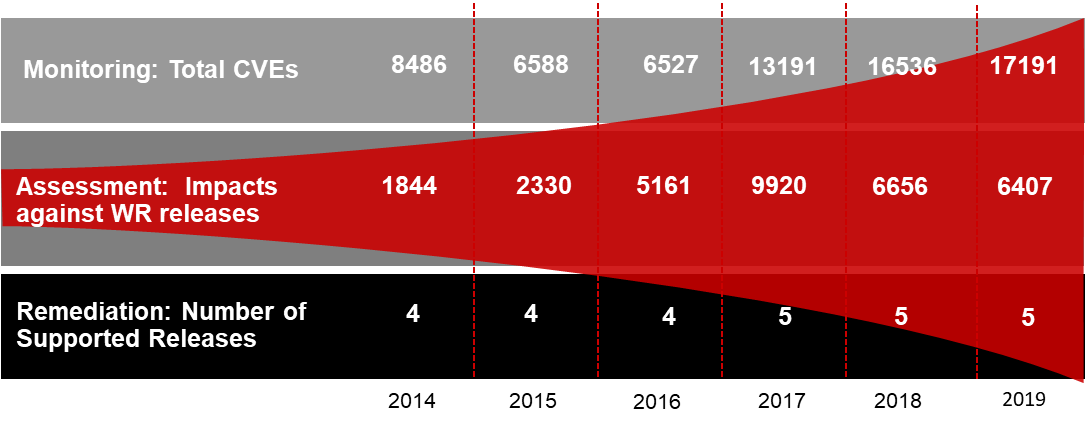
Management process for high security
To reduce threats on Linux-based systems, Wind River developed a management process and four-step procedure to: monitor, assess, notify and remediate CVE threats. Let's examine the process in more detail:
1. Active monitoring
Monitoring is essential and required due diligence for staying ahead of threats in this ever-changing world. Obviously, this alone doesn't solve any problems, but does provide critical insight of potential vulnerabilities and is a differentiator with a trusted-vendor. This is represented by the top row in Figure 1.
Neglect remains a big risk and some Linux providers are vulnerable from the very beginning with inferior due diligence. Wind River Linux customers are supported by our security team’s committed to active monitoring, rapid assessment and prioritisation, proactive customer notification, and timely remediation to achieve a strengthened security posture.
For example, the Wind River security team is constantly monitoring the Common Vulnerabilities and Exposures (CVE) database for potential issues affecting Wind River Linux and the VxWorks real time operating system.
In addition, the team monitors specific security notifications from US Government agencies and organisations like NIST, US-CERT, as well as public and private security mailing lists, for alerts from each of these organisations whenever a new security threat arises. All the kernel features, user packages, and Linux tools supported in standard Wind River Linux distributions are monitored for security vulnerabilities against all incoming reports.
2. Rapid assessment
Awareness is only the first step. As soon as a potential threat is uncovered, the level of danger associated with the threat, as well as which release or parts of the Wind River Linux version are exposed or vulnerable, must be determined, by the team in charge of threat assessment. The vulnerability is categorised and prioritised based on impact and ranked in order of importance based on the CVE priority level and the severity of impact to a business, system performance or exposure of data. This step is represented by the middle row in Figure 1.
As noted in the next steps, mitigation of the vulnerabilities in this context typically involves coding changes, but could also include specification changes or even specification deprecations (e.g., removal of affected protocols or functionality in their entirety).
3. Proactive customer notification
Once an assessment is complete, the system reports back to any affected subsystems or users. The report provides sufficient detail about the vulnerability, as well as a plan to thwart the threat. The harvested information also synchronises with the remediation process.
The notification process is more vital than ever, and may involve employing outside tools and people. This is a determination that would be made based on the assessment of the vulnerability. However, the critical element of this step is the timely handling of notifications with customers to keep damage or data loss to a minimum.
4. Timely remediation
The remediation process occurs, triage style. The Wind River team works to gather all the information relevant to the problem so that it can be analysed. Vulnerabilities may occur in Wind River-developed products or in execution environments in which Wind River products operate.
Based on the severity, threats are either dealt with immediately or handled in a timely 'bug fix' manner, which would be deployed in a later update. The less-severe vulnerability patches in Wind River Linux are delivered via monthly product updates. Keep in mind this remediation must be done against all current releases in the field. That is represented by the bottom row in Figure 1.
The standard Wind River Linux release model follows a one-year update policy, i.e., one release version every year. In effect, this means that every 12 months Wind River introduces a kernel update for the Wind River Linux base platform and other architectural changes deriving from this.
In addition, software patches and minor updates to current releases, with active maintenance, are delivered via Rolling Cumulative Patch Layers (RCPLs). These RCPLs are provided on an on-going basis according to a predictable schedule and do not trigger any major kernel, tool chain, or user space package revisions (unless a critical issue requires specific action).
Wind River Linux is also available as a continuous delivery subscription where updates are made every few weeks. Each update is treated as formal release, thus every few weeks a new release is made that must be included in any assessment and remediation. As DevOps and CI/CD increase in use, this will put additional burden on developers to manage the CVE process.
Customers clearly benefit from Wind River’s standard support for up to five years (which can be extended for the lifespan of the device). Regular maintenance, including the 4 step CVE process, can radically reduce the hassles, lower the costs, and protect customers from the risks of security vulnerabilities across their entire lifecycle.
Future plans
While the above management process and steps won't ensure that all threats are avoided, they do help mitigate customer risk and reduce a system's exposure. Wind River’s dedicated Linux support personnel and product engineers can reduce the development cycle time, provide threat due diligence and help avoid security breaches.
Developers may want to apply a critical lens when deciding to build and support their own Linux distribution or when choosing a commercial Linux OS provider. Supporting security vulnerability needs to be considered and compared to how they follow the steps outlined here.
For further information, please see the whitepaper on Wind River’s Linux Security page.
Courtesy of Wind River.










