IoT zombies are eating the Internet
Distributed Denial of Service (DDoS) attacks have always been a problem for popular hosted sites, but the ones from the last few weeks are different.
Guest blog by Alex deVries and Tim Skutt.
The first one to make the news was Brian Krebs’ krebsonsecurity.com, one of the most comprehensive security news sites today. The DDoS attack was on the order of 620Gbps, which cost Akamai too much to defend and resulted in krebsonsecurity.com going offline for a couple days. The source: hacked webcams acting as DDoS zombies.
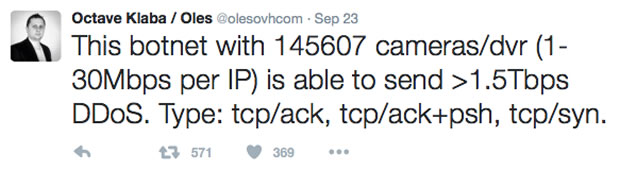
A second one was on OVH, a French hosting provider. They survived a 1.5Tbps attack. Their claim that the attack was from 145,000 hacked cameras and DVRs is consistent with Akamai’s observations.
Besides the scale, what’s different about these attacks? IoT
The advent of IoT brings with it incredible scale of powerful low-cost devices. A fleet of 150k command-and-control devices gives a great platform for an attacker. The devices are often scattered on the Internet, making them difficult to track.
Devices like cameras can be easy to hack. Devices have relatively long life spans and firmware is rarely updated, so devices often remain vulnerable to attacks long after known vulnerabilities are patched. Firmware can be reverse engineered, having either have been ripped from a purchased device or downloaded from firmware updates. Many devices also have default usernames and passwords to make this even easier.
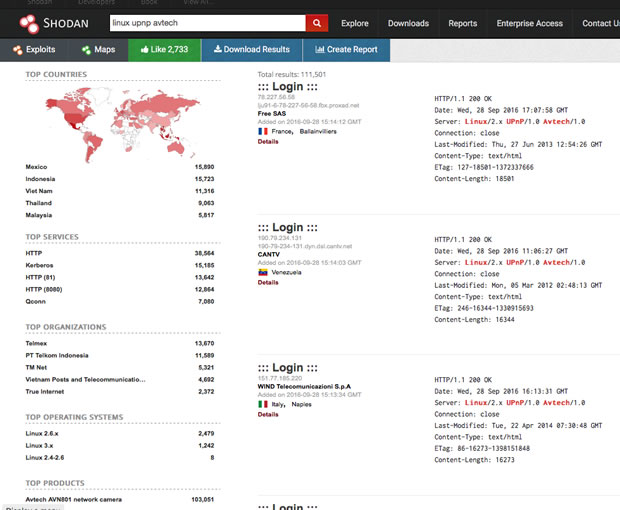
Targets aren’t hard to find, either. Sites like shodan.io make it trivial to find certain devices on the Internet.
Securing devices
There are best practices that can be followed to secure devices. Device identity, secure default configuration, secure updates and resource protection are just some. These work well for new designs.
Let’s also be realistic: in the meantime, there are millions of improperly secured devices on the Internet and they’ve been there for years. Fixing them is close to impossible. Even if with the perfect solution to hardening devices was available tomorrow, it wouldn’t help those.
Securing devices has benefits to IoT device owners, such as protecting their assets. But it hasn’t been their motivation to prevent DDoS of unaffiliated websites.
Protecting the assets
The best position for defence is usually around the asset. In last week’s case of Akamai (Krebs) and OVH, that was the website under attack and we saw the provider take action.
The motivation for securing devices, however, will come from IoT owners whose own assets are being threatened. It wasn’t immediately obvious to IoT owners that their assets were being threatened in last week’s attacks, but as vulnerable unprotected IoT devices are increasingly leveraged in attacks, it will become quite clear.
How? By recognising that targeted websites aren’t the only assets that will end up being protected – and the protection measures taken on other assets will impact IoT owners.
Network bandwidth is an asset. The 1-30 Mbps increase in bandwidth for an individual IoT device participating in an attack might not seem to be all that costly to the device owner, but when hundreds of thousands of these devices are aggregated, the expense of supporting an additional 1-2Tbps will almost certainly result in action being taken to protect network assets.
Protection of network assets against compromised IoT devices can take many forms, but for owners of network assets, this will often look like limiting access for suspect devices. This is where IoT device owners and IoT service providers will feel the pain.
IoT devices, by definition, get much of their value from being network connected. If network access is restricted based on device compromise, then much of the value of those devices will also be restricted. Value and revenue for IoT owners will be threatened.
Solutions
Securing new devices is critical, and solutions are available to ensure that new devices are secure when they are deployed and remain secure throughout their lifetime. These solutions involve:
- Secure device identity
- Secure configuration – including secure boot, secure initialisation, signed binaries, etc.
- Secure updates
- Resource protection
As we mentioned earlier, this only addresses part of the problem. It’s likely that even many new devices will be deployed without these fundamental protections.
What do we do about these devices, both old and new, that haven’t built security in? A viable solution is to protect them using a secure IoT gateway (either physical or in a virtual machine).This puts protections logically close to the IoT device and allows the IoT owner to protect their assets – including the network bandwidth they need to preserve value and revenue.
Wind River technology has security features available today such as secure device identity, secure configuration, secure updates, and resource protection. These features can protect new devices and ensure those devices stay protected. IoT solutions need to incorporate those protections so we can realise the full potential of IoT. We also need to recognise that there will be large communities of devices that, for a variety of reasons, do not incorporate protections and need a solution such as an IoT security gateway to implement security features on behalf of the device.
And those are the same kinds of device security features that will prevent IoT-controlled DDOS.
Courtesy of Wind River










