IoT Security – the next-gen of social responsibility
In response to recent events, the White House and the National Institute of Standards and Technology (NIST) have just released the much awaited and polished guidance around cyber security for the Internet of Things (IoT).
Guest blog by Neil McLellan.
Over the past several months, connected devices have been the focal point after several crippling attacks on various ISPs, known as distributed denial of service (DDoS) attacks. One of the key points that NIST calls out is the lack of designed-in security, which not only opens IoT devices up to attack, but also increases the longevity and intensity of an attack.
These failures set the stage for the 21st October attack on Dyn’s DNS systems – effectively bringing down the internet by weaponising unsecured IoT devices as relay agents.
IoT connected devices include common products that are now capable of internet connectivity – washers, dryers, coffee pots, and automobiles – devices historically not built with a high degree of cyber-security in mind. This year alone, we saw a 30% uptick in growth of IoT-enabled devices – roughly five million new devices every day. In addition to the growth of IoT enabled devices, there was an additional 30% jump in DDOS attacks since 2015 – 1000 times the order of magnitude of the year prior.
Special Publication 800-160 seeks to provide guidance enabling the design of ‘more defensible and survivable systems’ throughout the life-cycle of connected systems. As such, the majority of systems and devices presently depend on post-manufacture preventative measures and counter-measures to prevent security breaches. This guidance not only addresses this requirement on new systems, but also the implementation of modifications to currently deployed systems and disposal of retiring systems.
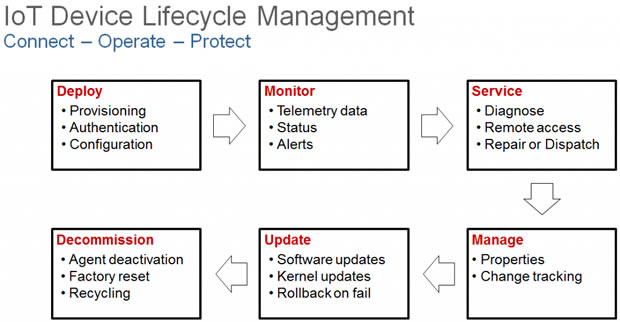
As the number of fielded IoT devices reaches 20-25 billion assets by the year 2020, response to cyber security events will scale beyond the ‘boots on the ground’ approach – remote device management will be a necessity. Wind River has pre-emptively published guidance around identifying and mitigating vulnerabilities early on, with regards to an IoT-enabled strategy; see our recent white paper focusing on IoT and Cybersecurity.
With no formal standards in place to govern the security conformance of IoT devices, it is incumbent upon device manufacturers to take proactive steps to unilaterally secure devices and include mechanisms to mitigate evolving cyber-security threats across their IoT portfolio.
Keeping recent events in mind where inadequate or lack of security measures were included in IoT device design, these proactive steps define the actions of socially responsible corporations in ‘the new world’ – looking after our shared IT ecosystem. The proliferation of IoT-enabled devices lacking these considerations have already proven how quickly unsecured devices can work against us.
The designed-in security across the Wind River embedded portfolio provides the latest version of Wind River SSL, enabling the latest in encryption, in addition to Wind River SSH, Cryptography Libraries, and Wind River IPsec and IKE to secure all data in-flight communications. Additional device-side protections are provided with Secure Boot, which prevents the injection and execution of malicious code – allowing only signed binaries to run.
Completing the end-to-edge manageability plane, Wind River Helix Device Cloud enables device makers complete and total remote device management capabilities, including:
- Immediate notification of threats and issues on mission-critical devices.
- Secure two-connectivity to remotely diagnose and repair devices.
- A SOTA/FOTA capability to apply fixes and patches combating potential vulnerabilities on one device, or the entire portfolio of IoT devices.
- Remote decommissioning of a device and data destruction associated with physically compromised devices.
Courtesy of Wind River.










