Immunisation against the IoT Zombie Horde
IoT zombies are out there. There are a lot of them. We won’t be rid of them soon. They will be reaching out to your device, so it’s important to take steps now to immunise it so your device won’t suffer.
Guest blog by Alex deVries and Tim Skutt.
In a previous blog, “IoT Zombies are Eating the Internet,” we dug into recent large scale Distributed Denial of Service (DDoS) attacks that leveraged IoT devices as bots, or zombies, in their attack. Soon after we wrote that blog, the source code for the attack was released by someone claiming to be the malware’s author. The malware, Mirai, is a virus that carries a Trojan to get IoT devices to perform a DDoS on several high-profile sites. The estimates are huge; Malware Tech estimated 120 thousand devices were infected, but Level 3 says 1.5 million devices. This is just a recent example.
These viruses are forever.
As we consider how to deal with the onslaught, it’s helpful to use medical virology to get a better look at how Mirai has spread. Medical infections are modelled on a susceptible, infection and recover curve. That works well here too:
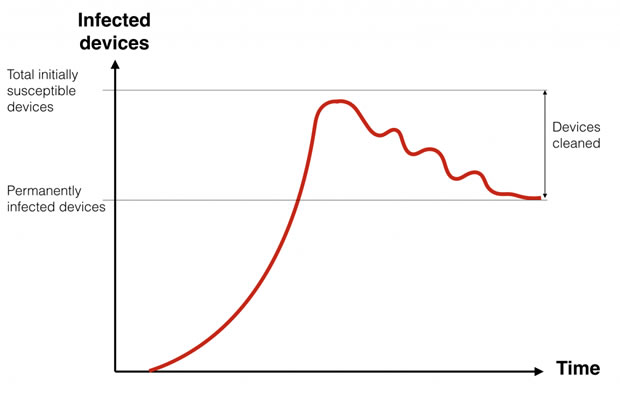
Once a device has been infected by Mirai, it randomly sprays the Internet looking for devices with open Telnet ports using default credentials. Once found, it infects them, turning them into zombies which, in turn, spray the Internet to look for more targets. This is shown in the first major ramp.
Some devices will be cleaned or protected, but many never will be. These are the permanently infected devices.
Even if a device gets cleaned, if it’s not immunised, some other infected device will likely re-infect it. Since many affected devices will never be updated to remove the infection, the epidemic will continually renew itself for the foreseeable future.
Can we kill it?
There may be some ways to kill Mirai, or at least limit its impact.
Fix all the devices
Practically speaking, this will never happen. Most of the device owners won’t know their devices are infected, won’t have the skills or ability to fix them, or won’t care to fix them (since it doesn’t affect them directly).
Kill the command-and-control servers
A weakness of Mirai is that a freshly infected device needs to register with a command-and-control server to download instructions. These are compromised servers, not likely infected devices. If command-and-control servers are killed, it will limit Mirai’s proliferation.
Protect the target
In response to the recent IoT DDoS attack, the security site krebsonsecurity.com was moved to a different hosting company to avoid the attack. DDoS attacks are nothing new and there are ways to mitigate against this, such as moving the target.
Ultimately though, fixing all the devices currently infected or potentially infected is impractical, and it’s unlikely we can fully kill the infection.
Things to come
If it isn’t Mirai, some other self-propagating malware will be developed to infect other IoT devices. Mirai’s source code was released, which accelerates development of subsequent viruses.
Widespread availability of Mirai’s source code will inspire adaptation. We can expect that the dependency on a command-and-control server will likely disappear. This mutation will make it even harder to kill.
So far, Mirai has been focused on DDoS attacks, but next is leveraging IoT devices to attack other systems on the same network as the zombie IoT device.
Immunise your devices
It appears that IoT zombies will be around for the foreseeable future. We can do our best to avoid them and even quarantine them, but as networks change and new devices are deployed, new paths for exposure will open up. Since the threat of infection will be persistent, it’s only a matter of time before your device will be targeted. Immunising devices against infections is critically important.
The first step of immunisation may sound obvious – eliminate the known methods of infection. Eliminate or block unnecessary services (such as Telnet), eliminate default credentials and replace them with robust passwords, block unexpected connections to outside endpoints.
As we look to the future though, a second step of immunisation is needed – preventing vulnerabilities that an adapted virus may leverage. This is where tools such as the CWE/SANS Top 25 Most Dangerous Software Errors can help. This is also where Wind River can help.
Wind River products provide multi-layer, pre-integrated defenses that include:
- Secure boot and initialisation to protect against compromised executable code
- Data-at-rest encryption to protect credentials and other sensitive information
- Mutual authentication to protect against counterfeit endpoints as well as malicious attempts to connect
- Data-in-motion encryption to protect sensitive information
- Hardening of the operating system to prevent privilege escalations
- Firewall to block unexpected external access as well as unexpected connections to the outside world
- Secure updates to prevent malicious modification while still supporting authorised changes
These defences are incorporated in Wind River’s customisable operating system products that allow unneeded services to be excluded from a device. This minimises the possible ways an infection can compromise your device, while still providing the device a robust set of defences.
In addition, Wind River has a Professional Services organisation that can help with assessment and customisation of products to fit the needs of your device – from tools and processes for establishment and deployment of security credentials, to optimising the use of hardware security capabilities, to security threat assessment and security testing.
The Talking “Dead”
IoT zombies will be reaching out to your device, talking to it, and trying to find a way to infect it. There are ways to protect your device and pre-integrated solutions that can immunise it against not only today’s strain of the virus, but also against upcoming mutations. Immunising now will ensure your devices stay healthy for the long haul.
Courtesy of Wind River.










