Cyber security for TSN in modern automation networks
Time-Sensitive Networking (TSN) is the next evolutionary step for Ethernet technology and it is well on its way to establish itself as a fundamental building block for Industry 4.0 and IIoT (Industrial Internet of Things) networks.
Authors: Dr. René Hummen, Dr. Oliver Kleineberg.
While introducing real-time communication properties and guarantee of service, this new technology, however, also creates new cyber security challenges.
But fret not, these challenges can widely be managed with existing and proven security mechanisms as well as with established best practices for industrial network security as discussed in this article.
Time is of the essence
TSN is comprised of a family of standards that is specified in the IEEE 802.1 and 802.3 working groups. Some of these standards have recently been published, whereas others are still in preparation. Common to most of these standards is the need for a shared time base on all devices that participate in a TSN network. This common understanding of time is necessary to be able to transmit data frames deterministically along a scheduled path, adhering to a clearly defined upper latency boundary (delay time) and achieving low jitter (delay variation).
To provide these properties, TSN utilises TDMA (Time Division Multiple Access) splitting time into repeating cycles. Time slots in these cycles are then reserved for high priority data streams, which need to be protected from other network transmissions. Such reservations happen for all network participants along the transmission path. In other words, a reservation creates a virtual circuit between two or more end-devices through the TSN network. To make sure that each device adheres to the reserved time slots, the internal clocks of all network devices need to be synchronised. The high precision, which is required for TSN regarding time synchronisation, is typically achieved using IEEE 1588, better known as the Precision Time Protocol (PTP).
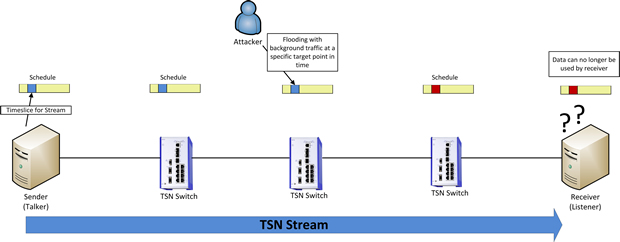
Time as an attack vector
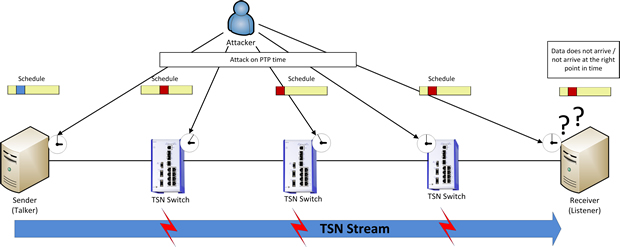
When aiming to impede the operation of today’s networks, Denial of Service (DoS) attacks are a widely used tool. DoS can, for instance, be achieved by flooding the network with large amounts of data, thus overloading it to the point where it can no longer perform its function. As TSN relies on synchronised clocks, both the PTP synchronisation protocol as well as the TDMA mechanism are new attack vectors in a TSN network. As a result, it already suffices to target and deliberately overload a single reserved time slot in order to impact a specific mission-critical communication stream. Besides the targeted overloading of certain time slots, the IEEE1588 protocol for time synchronization is a potential attack target itself as well.
Many automation networks today already use PTP. For this reason, it will be utilised in many applications for the synchronization of TSN clocks. Yet, by design, PTP has no integrated security mechanism and relies completely on the security mechanisms that are present in the network.
With no means of network security in place, a potential attacker could, therefore, hijack the function of the central time source, the 'grandmaster', using falsified PTP data packets. The false grandmaster could then send time synchronisation information with large jitter into the network, thus sabotaging the proper alignment of the time slots on the individual devices. Furthermore, the attacker could enforce time discontinuity, which would result in many time-sensitive end-device applications to go to a safe shutdown state immediately.
So, what does that mean for cyber security in a TSN network?
Network protection
For the most part, traditional security solutions such as firewalls will remain key mechanisms for securing a TSN network. The real-time properties of TSN, however, have an impact on the design of some of these security measures. For example, if data packets that are passing through a firewall cannot be checked in real-time, because the software has to look into the payload of each forwarded packet (Deep Packet Inspection, DPI), the resulting computational overhead creates an additional transmission delay. If this delay is not taken into account when time slots are reserved, there is a risk that data packets will be delayed to a point, where they move into reserved time slots for which they were not intended. One possibility to get on top of this issue is to employ firewall technologies that are guaranteed to work in real-time. Another possibility is to make the additional delay visible in the network, such that the calculation of the TDMA schedule can be adjusted accordingly when reserving a stream.
This type of delay transparency also applies to switches, which support security mechanisms at the hardware level, for example, Access Control Lists (ACL) and stateless packet filters. Even though these mechanisms usually operate at wire-speed, a slight delay may still be introduced. This has no impact on regular Ethernet networks. In TSN networks, where data transmissions rely on microsecond precision or even less, data communication could, however, be disrupted. Nonetheless, this does not imply that established security mechanisms can no longer be used in a TSN network. Nothing is further from the truth. It is rather important that the additional delay introduced by an on-path security function, including firewalls, is considered in the latency and scheduling calculations of a TSN network.
Depending on the specific application requirements concerning transmission latency and cycle time, a huge transmission delay may, however, not be tolerable even if it was made visible. Here, two classes of network security functions have to be differentiated: first, mechanisms that are directly implemented on the TSN communication path, and second, mechanisms that are located at the boundaries of a TSN network. Security mechanisms that are located on the communication path must only induce a low and calculable transmission delay. In contrast, longer delays may be tolerable at the boundaries of the TSN network.
This distinction between different classes of network security functions also corresponds to the security best practice 'Zones and Conduits' and adds an additional aspect to this security discussion: The subdivision of a network into communication zones is intended to establish separate communication areas and only enables communication between these areas on a 'need to communicate' basis, thus further ensuring network security. In doing so, the 'Zones and Conduits' best practice today primarily focuses on hardening the cyber security of a network. With TSN, the “timing of communication” will be an additional parameter to consider.
It is, therefore, important to observe that TSN and 'Zones and Conduits' go hand in hand, as the 'need to communicate' and the 'timing of communication' are both based on the same end-to-end communication relations of network devices. Consequently, a secure network design should place, for example, DPI firewalls at the interconnections between the different communication zones, while fast stateless ACL packet filters should be used inside the zones, where they are located directly on the TSN data path.
Coincidentally, this way another best practice security concept is implemented, namely 'Defense in Depth and Diversity'. This best practice recommends combining security mechanisms that operate differently and connect them in series in order to secure a network. Following the best practice of 'Defense in Depth and Diversity' classic network access layer security mechanisms such as IEEE802.1X that are often implemented in switches and routers should also be used to protect the direct access to the TSN network. Moreover, layer 2 security mechanisms should be employed to further harden the TSN network against attacks.
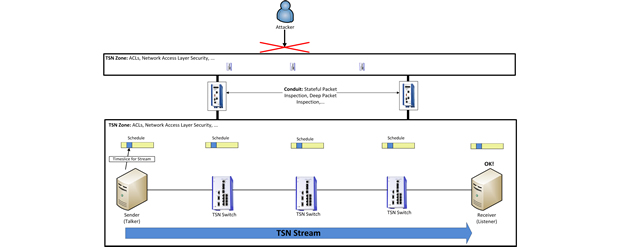
Layer 2 security
One of these mechanisms, which is are currently being developed as part of the TSN standardisation effort, is “Ingress Filtering and Policing” (IEEE 802.1Qci). This technology allows to check if data frames as well as their time of reception match a reserved data stream. If this is not the case, the packet is filtered and rejected before it leads to any negative effects on the network operation. Additionally, mechanisms such as MACsec (Media Access Control Security) can be used to authenticate, encrypt and integrity-protect the various data streams between the network participants.
Especially security mechanisms such as MACsec, however, again can have negative impacts on the end-to-end transmission latency in a TSN network, even if they operate in hardware. Hence, as discussed above, the additional delay introduced by these mechanisms has to be made visible as well. In doing so, the additional delay that must be considered strongly depends on whether the security mechanisms are based in software or hardware. Overall, the cornerstone of TSN cyber security is: if the introduced latency impact can be taken into account, nothing stands in the way of a smooth and secure TSN operation.
Summary
TSN is the next evolutionary step of Ethernet technology. The high bandwidth and real-time services that this new standard provides are the prerequisite for the modern automation networks of the future. Since TSN is not a manufacturer-specific technology, it can be universally utilised in all automation networks. To guarantee cyber security in a TSN network, the wheel does not have to be reinvented. The contrary is the case: security mechanisms that are state of the art today will ensure the secure operation of a TSN network. Still, the strict requirements for real-time communication add a new layer of complexity that needs to be considered in the network design. This new aspect, however, fits seamlessly into existing concepts.
Although the entire family of standards for TSN is yet to be completed, the released standards can already be used. Moreover, as the specification of the remaining TSN standards is well under way in the IEEE 802.1 and 802.3 work groups, the standardization process ensures that future TSN security mechanisms will be compatible with standard Ethernet.











