Security in the era of cognitive IoT
The connectivity of things such as thermostats, medical devices, automobiles and industrial equipment presents an exciting environment for innovation and new business opportunities. As we rely on connected devices to make our lives better and easier, security must be considered from every aspect.
There have been examples of security incidents associated with the Internet of Things (IoT), however, if you are well prepared, follow best practices, and leverage the right solutions from trusted partners, you can be more prepared to prevent such incidents. If the worst does happen, you have insight to detect, respond to, and recover from the incident in a controlled and risk-aware manner.
Security is everyone’s responsibility
Every participant in the IoT ecosystem has a responsibility for the security of the devices, data, and solutions. This means that device manufacturers, application developers, consumers, operators, integrators and enterprise businesses all have their part to play to follow best practices.
IoT security requires a multi-layered approach. From a device point of view, it should be considered at the blueprint level that starts with design and development and keeps hardware, firmware/software, and data secure through their entire life. The same approach applies if you are a security analyst or operations personnel responsible for IoT solutions. To enable the full potential of IoT, security challenges must be addressed through a combination of interoperability, education, and good design — and by taking a proactive, not reactive approach to designing security features, which will result in better products and solutions.
The beauty of IoT is its simplicity, ubiquitous nature and ability to digitalise the physical world. IoT can represent objects in a digital format as data which can be analysed for business value and improve quality of life. Because IoT sensors are embedded in a plethora of devices and locations it is inevitable that these devices will be exposed to harsh conditions. In contrast to traditional IT assets, there is not always a human operator to check on IoT devices, to interact with them and make sure they are performing or as protected as they should be. It is imperative that if a device is compromised by natural elements or human intervention, the compromise is detected as quickly as if it occurred inside a controlled environment.
The spread of devices increases the surface area to protect
IoT, by its very nature, is comprised of multiple devices, from manufacturers leveraging diverse firmware, software, operating systems and varying degrees of compute power. IoT devices that could be considered “primitive” devices can send out kilobytes of data a minute to complex things comprised of multiple sensors churning out gigabytes of data in a continuous data stream. This data and value can help provide insights to transform industries. This is a step away from traditional IT endpoints which are comprised of, in practice, only a few variants (desktops, laptops, servers, mobile devices – running Windows, Linux, MacOS, iOS, or Android). The variety of IoT devices and their use also presents a larger surface to protect. Possible attacks include obtaining private or confidential data, manipulating or controlling devices, or confusing or denying service to applications that use and supply data within IoT systems.
There are different requirements for IoT security depending on the risk profile of the system being secured. For example, the security needs for a consumer IoT system to measure and control a watering system for garden plants are different from the needs of a complex, mission-critical, enterprise petroleum drilling or pipeline operation that involves IoT-connected valves and pumps. So there is always a need appropriately balance the level of security, the usability and value of the solution and the potential risk or damage to your organisation in the event of an incident. However, as seen in recent attacks publicised in the media, no matter the intended use of devices, if those devices are vulnerable to being taken control of, they could be used to mount attacks or cause havoc on other systems altogether.
Understanding the intricacies of IoT and the security around it is something that we at IBM have taken very seriously. We have invested and combined the expertise from across the IBM business incorporating thought leaders from IBM Research, Security, and IoT to provide a comprehensive overview of IoT Security. In our latest POV on cognitive security for the Internet of Things, we share with the whole IoT community in a bid to disseminate ideas and best practices. In addition, we continue to work with various organisations who are researching and publishing recommendations on IoT and security including the Industrial Internet Consortium (IIC) and IoT Security Foundation (IoTSF).
Taking all of this into consideration we have simplified the approach by focusing on three key elements:
- Device and data protection: Begin by securing the devices and data from the context within which they have been deployed. Ensuring secure connectivity to IoT platforms, payload encryption, device identity using certificates and segregation and encryption of data in transit and at rest.
- Proactive threat intelligence: Leverage tooling to visualise and prioritise threats aiding security and operations experts to focus their attention on the real-time issues. Have, where appropriate, automated responses to provide proactive protection whilst not impacting business operations.
- Cognitive risk management: In the future, we envisage the use of cognitive computing as a key asset in your IoT security toolkit to be able to learn from the security intelligence gathered within your IoT landscape and provide better insights to proactively deal with threats as they adapt. We foresee that in sheer numbers alone, it will not be possible to rely on human response to deal with situations experienced by the plethora of connected devices deployed for IoT solutions. This demands that systems detect and respond to situations observed and is an area where we expect cognitive computing to provide assistance in handling the complexity and scale of the challenge.
These elements should be considered as a journey requiring consistent attention and multiple iterations through a continuous lifecycle/delivery approach. History suggests that organisations must be vigilant in addressing safety, security, and privacy. The recent set of attacks reinforces this need. New and emerging threats and attacks which change over time (see Figure 1 below), thus the need to continually adapt and evolve.
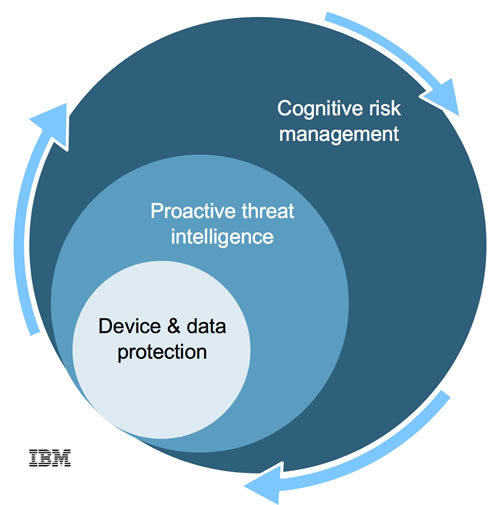
Figure 1: Levels of IoT security graphic
Security by design
IoT solutions are broad, complex, and often global — requiring a robust set of measures to ensure integrity and safety. IoT platforms are a key component for any IoT solution. The Watson IoT Platform has security by design engineered into the platform and the infrastructure upon which the platform is based. To help security analysts and operations personally address the wide variety of IoT security threats, we are building advanced security capabilities using dashboards and policies that will soon be in a beta. Our intent is to visualise the security risk profile of an organisation’s IoT landscape, and provide policy management tools that allow checks to be defined and responses to be, where appropriate, automatically carried out. We also offer professional services around data anonymisation, threat intelligence, blockchain in addition to a security assessment.
You must be proactive to ensure your IoT deployment and company are resilient and resistant from attack. Embark on your IoT Security strategy today.










