How the IoT has increased the importance of security
Steve Rogerson looks at how the conference and exhibition at embedded world 2016 will face up to the increasing emphasis on security.
Once, security at an exhibition was more about having bags checked on the way in rather than what was displayed on the stands. But no longer. As the IoT spreads its wings bringing connectivity to all areas of people’s lives, so does it open up the same people to malicious intrusions. If it is connected, it can be hacked, as recent high profile cases have shown.
There is therefore no surprise to see security such a hot topic at this month’s embedded world in Nuremberg. As well as dominating large chucks of the conference, many stands will be featuring either ways to secure connected products or displays ensuring potential buyers that their products are indeed secure.
Conference
One presentation by Robert Day from Lynx Software Technologies and Dan Isaacs from Xilinx will be looking at using the multi-layer security on programmable SoCs for architecting cyber secure IoT systems.
“Last year was very interesting in terms of cyber security for connected things,” said Day. “It hit the headlines with the Jeep hack and people wanted to know what was going to be done about it. We have spoken with motor manufacturers and tier ones over this.”
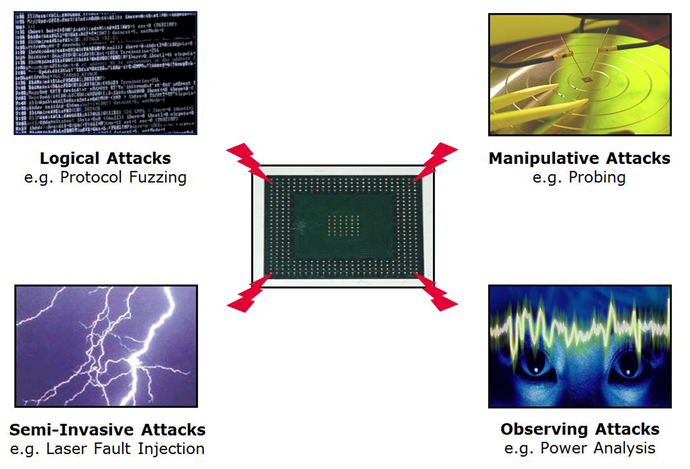
Above: the four main attack groups according to Marcus Janke from Infineon
The Jeep hack, he said, was significant because other car hacks had involved some form of direct physical connection with the vehicle, but with the Jeep, the hack was done wirelessly.
“This can spread across the whole connected world,” said Day. “Suddenly, all the usual security systems are bypassed. You are saying ‘Come on in’ to the hack community.”
A key element therefore in security, he said, is separating the IT and OT networks, using products such as Lynx Secure, which was designed for the military world where networks with different levels of security were coming into the same device and were not allowed to talk with each other. This was done using a separation kernel with virtualisation.
“Most companies with a separation kernel rely on the operating system underneath it,” said Day. “That can be hacked. Our separation kernel has no operating system at all. If you hack into one of the operating systems on top of the kernel, you can only see the domain you are in and not get into the others.”
One change, though, since last year is that such systems normally ran on Intel processors.
“Arm is now catching up with Intel on the ability to separate devices on a single platform,” he said. “We picked Xilinx because their latest ARM-based processor is geared towards security.”
Lynx is also doing a joint presentation with Webroot because its software lets the user know an attack is going on even if it has been stopped.
“It shows who is attacking you and what sort of attack it is,” said Day. “This is in the enterprise world and we are trying to bring it into the IoT world.”
The presentation from Marcus Janke and Peter Laackmann from Infineon Technologies will depict the evolution of attack methodologies against embedded devices, focusing on the security of embedded microcontrollers.
“We have both worked in the security area for more than 25 years,” said Janke. “It started as a hobby with pre-paid cards for the public telephone system in Germany. There are now a lot of other smart cards for banks and so on and some of the attack methods can be applied to embedded devices.”
Above: network security graphic showing a TLS protocol exchange that provides communications security over the internet. HCC communications stacks use a verifiable development process proven in industrial, transport, medical and aerospace industries to reduce coding errors and limit security breaches
He said there were four different classes of attack. First was a logical attack that sends something over the communications to try to trigger a function. Secondly, manipulation attacks are where the attacker tries to influence the silicon by opening up the chip and using probes.
The third area of attack is observation where the behaviour of the chip is monitored to try to figure out what is happening. And fourth there are port injection attacks to influence the programme flow and create a glitch.
“We will look at how you can defend against these,” said Janke. “With smart cards, it was about personal data. With embedded devices it can be trade secrets or IP that needs protecting. Someone could also try to change the behaviour of the chip. Say the chip is part of the security for a larger system, they could influence the chip to bypass the security.”
He said a lot of systems relied on software security running on a normal CPU that was typically not protected.
“It is more secure if there is dedicated hardware,” he said. “That acts as a trusted anchor. It would be more difficult for such an attack.”
Exhibition
There will also be security announcements on the show floor. HCC Embedded, for example, will be releasing an IPSec module to extend the security of its network stack so it will have a full set of security protocols that can handle all popular forms of secure network traffic.
However, Managing Director David Hughes does believe some of the security issues are exaggerated. “Some people are scaremongering,” he said. “Some think everything has trojans that China and the US can switch on and stop things working. I don’t believe that at all.”
Security is a big issue in automotive with the move towards autonomous driving and the Jeep hack bringing this sharply into focus.
“The Jeep hack was ridiculous,” said Hughes. “The whole system was poorly designed. They appeared to have no understanding of security. This was a pure design failure.”
Survey
What could help set the tone at the event will be the release of the results of an industrial survey on embedded software and security. This has been run by training and consultancy company Barr Group.
“We are trying to gauge how important people see security and safety as the number of IoT devices proliferate,” said Barr Group CTO Andrew Girson. “And we are looking at the intersection of security and safety. Is one more important than the other?”
Conclusion
Whereas in the 1990s, the industry concentrated on packing more functionality into systems. This changed in the 2000s with more connections being set-up and thus now in the 2010s the question of security has become dominant. With a large chunk of the conference at embedded world being devoted to security, it does seem that the industry is taking it seriously. And it needs to, because every Jeep hack reduces confidence in what the industry is doing.










