Under inspection
Tackling rising network traffic with high-performance deep packet inspection for increased security and intelligent packet handling. Steve Konish, Director of Product Management, Communication Platforms, Wind River, discusses further in this ES Design magazine article.
The network infrastructure is becoming overwhelmed by ever-increasing data traffic, resulting in a growing number of security breaches and attacks of malicious content. Equipment providers aiming to deliver increasingly intelligent solutions for mobile, fixed and enterprise networks are searching for new software-enabled deep packet inspection (DPI) solutions such as pattern matching and content scanning to meet these challenges. Using high-performance multi-core technologies, software-enabled DPI can also deliver significant advantages in the area of application identification, traffic shaping and policy server implementations, enabling providers to better manage networks as well as being able to add new services, including those at tiered levels.
Billions of devices and machines are now connected to the network. This number is expected to triple in the coming few years as connectivity continues to rapidly expand beyond PC, smartphones and tablets and deeper into the world of machine-connected devices of the ‘Internet of Things’. These devices and machines will generate massive amounts of new data traffic on the network. The impact on the existing infrastructure will create serious challenges for equipment providers and network operators - in fact, the explosion of connected devices will generate a level of traffic that has the potential to bring existing networks to their knees. As the demand for network usage increases, new services will be needed to deliver higher value, greater security and better quality of experience. Meeting these challenges will require new and more intelligent solutions, driven by advances in software that take full advantage of new processing technology and effectively employ technologies such as DPI.
Use cases for DPI
There are two primary use cases for DPI: firstly using the technology for various different kinds of security applications; and secondly using it in policy servers and flow analysis to analyse and direct traffic and bandwidth. And for these use cases there are three key target markets, which are: Communications systems of all kinds; enterprise networks, which could be any kind of campus network or metropolitan area network (MAN); and wireless networks, such as 3G, LTE, radio-access and mobile broadband networks.
While these target markets utilise different network elements, all still have requirements for both security and policy server/flow management. As an example, a security DPI solution is critical to the enterprise network with its various requirements for firewalls, threat management, virus protection, and intrusion detection and protection. This is also the case for radio networks, but only in certain places at the access layer, such as where the radio-network front-end is accessible in a particular area or cell. Mobile broadband also requires different types of devices that demand both security and policy management.
According to the latest report from Infonetics Research, which tracks DPI software solutions and related hardware deployed in wireless and fixed-line networks, service provider DPI revenue was up by 28% in 2012, totalling $596 million. While fixed-line operators are still a significant portion of the DPI market for data traffic management, it is mobile that is expected to drive the DPI market over the next several years. In the same report, the wireless segment of the DPI market was forecast by Infonetics to grow at a 33% CAGR from 2012 to 2017.
Certainly, a fast growing trend in the industry is the ability for network operators and Internet providers to offer differentiated levels of service. QoS (Quality of Service) policy filters that employ DPI technology to determine the origin of the packets are becoming increasingly pervasive, enabling improved levels of subscriber-aware traffic management. During peak usage times, for example, the technology could enable providers to give a lower priority to data that is associated with only a certain level of subscriber service, perhaps for high-bandwidth applications such as video streaming.
Deep inspection
As the names suggests, DPI analyses entire packets and correlates information across multiple packets to identify the application, whereas ‘shallow packet inspection’ only analyses the header of a data packet. The traditional security firewall for example will look only at packet headers. Advanced security application equipment will use DPI technology to examine the content of a data stream to detect threats rather than basing security decisions solely on fields in the header. The detailed examination of packets has an added cost, however, because scanning the content of data streams is CPU intensive and can become unfeasible as the load increases. The effectiveness of DPI therefore depends largely on how well it performs under heavy traffic.
To prevent this from occurring and to increase performance, network security vendors typically relied on hardware-assisted DPI technology to perform detailed content scanning at network speeds, using expensive purpose-built silicon such as application-specific processors, custom ASICs or FPGAs. In addition, this hardware has not offered the high levels of flexibility needed to adapt to the changing needs of networks, as well as being a solution that often leads to significant development and manufacturing costs.
However, DPI has been undergoing a rapid evolution in the market with the availability of advanced and high-performance multi-core processors from silicon vendors such as Intel. This has created the opportunity for well-designed DPI software to approach and even exceed the performance of previous hardware-based solutions. A software-based approach to intelligent and high-speed DPI can therefore provide a cost-effective and scalable solution that also has the flexibility to evolve with changing system requirements, especially in the security area where new malware and viruses are occurring constantly.
Intelligent pattern matching
Central to many DPI implementations is pattern matching: the ability to compare and match incoming data streams with a database of known offending patterns called signatures. These signatures represent potential malicious content and can take the form of simple literal strings or more complex patterns such as a specific arrangement of bytes broken up by a variable amount of other possibly irrelevant data.
While literal searches can be quite intensive, regular expression searches require significant processor resources that can become problematic to perform at high speeds, especially when searching for thousands of signatures.
An example of a leading software pattern-matching solution that compares large groups of regular expressions against blocks or streams of data is the Wind River Content Inspection Engine (CIE). Designed for low-end single-core to high-end multi-core processors, it is a scalable and cost-effective DPI approach that runs entirely in software. CIE can be scaled from less than 1Gbps up to 160Gbps, depending on the number of cores being used. While the engine has been designed to take full advantage of Intel multi-core processor technology, it is also processor architecture and operating system independent, therefore providing the opportunity to upgrade units already installed in the field. Additionally, easy to upgrade software updates provide continued performance improvements and functionality.
Ideal for applications that need to scan large amounts of data at line rate, such as intrusion prevention (IPS), antivirus (AV) and unified threat management (UTM), among other DPI systems, it delivers a cost-effective software solution for scanning data content at line rate in security equipment ranging from small network appliances to large network elements.
Application acceleration
As well as the issue of security, the growing number of connected devices means that network operators also face significant challenges to increase performance and find efficient and scalable ways to handle the on-going explosion in network traffic. This is in addition to expanding their network services to achieve higher average revenue per user (ARPU). Performance, however, remains a vital priority. Building in greater intelligence with DPI is highly desirable, but operators will not want to sacrifice speed for it.
Wind River Application Acceleration Engine is a comprehensive, optimised network stack designed for the acceleration of ISO-model layer 3 and 4 network protocols and the applications that run above them. Delivering major performance boosts compared to the native Linux network stack, the Application Acceleration Engine can provide up to a 1100% improvement in IP-forwarding for select packet sizes, up to a 500% improvement in throughput for User Datagram Protocol applications and a performance boost for TCP. Use of this engine means that network applications of all kinds, both legacy and next generation, can significantly improve performance and enable a number of new, high-value and extremely intelligent network services.
The Application Acceleration Engine works in the data plane in conjunction with Linux. While not exclusively, the software engine has been fine-tuned for Intel multi-core processors and communications platforms. Specifically the engine builds on the performance of Intel Data Plane Development Kit (DPDK) to accelerate networking applications of all kinds, and security components such as DPI and virtual private network (VPN) technologies. The Intel Data Plane Developer Kit (DPDK) is a set of highly optimised user-space libraries and drivers that enable the consolidation of control and data plane platforms and execute efficient packet processing on Intel architecture (IA) processors.
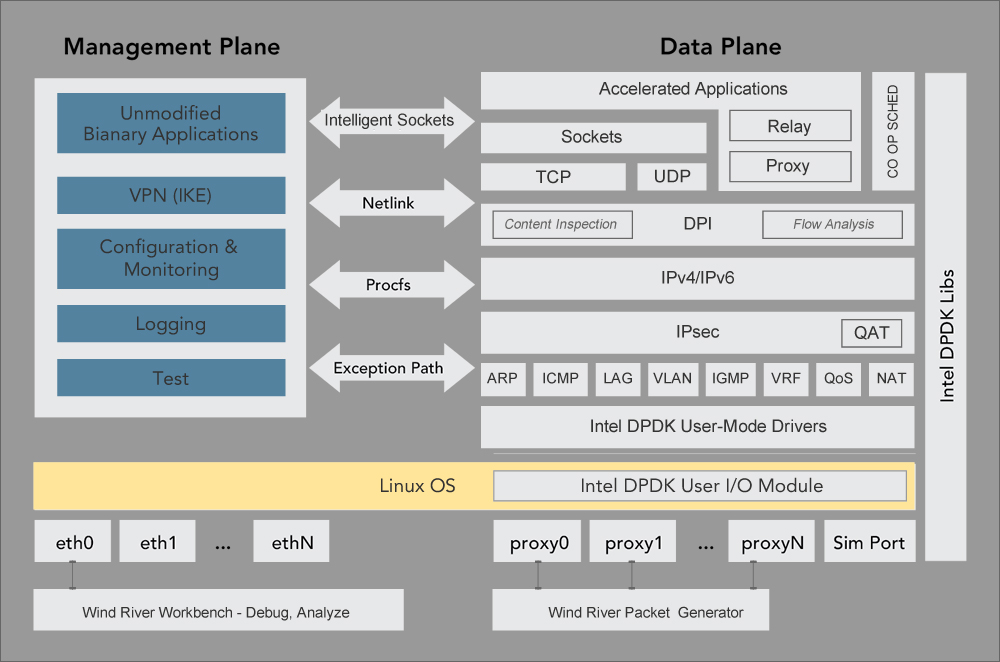
Figure 1: Application Acceleration Engine from Wind River
The Application Acceleration Engine can effectively isolate optimised application protocols including TCP and UDP and IPsec on a processor core and execute them in non-blocking mode without the need for context switching via the Linux operating system or IP stack. Delivering almost hardware-level throughput, it essentially takes the packet from memory or from the Ethernet port straight up to the DPI application through the optimised protocol stack, meaning the application can process the packet in almost real time. The Application Acceleration Engine is shown in Figure 1.
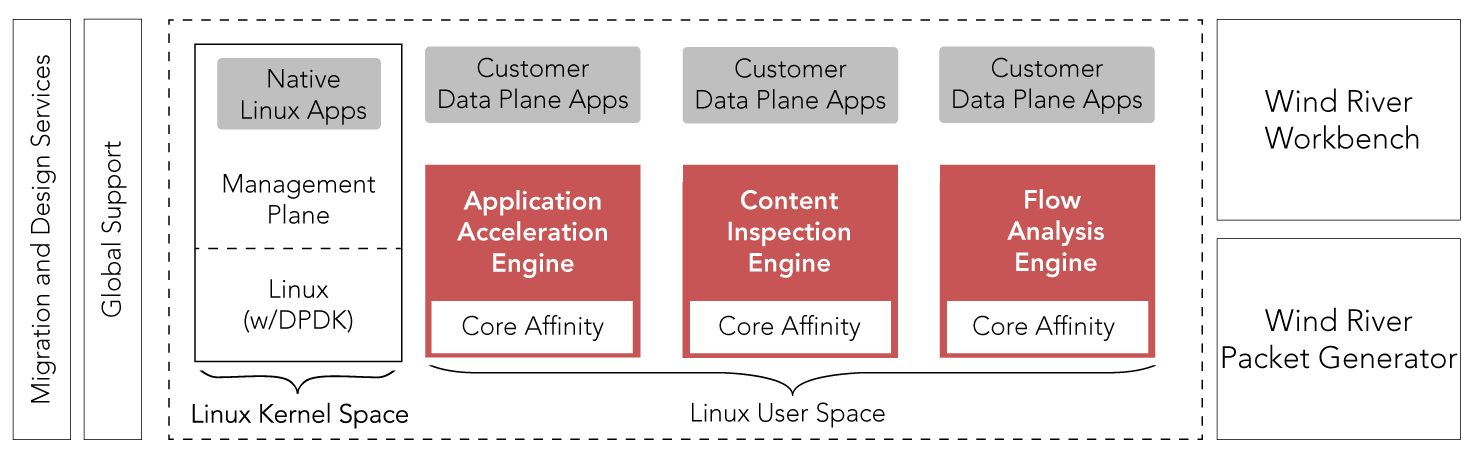
Figure 2: Key components of the Intelligent Network Platform
The Wind River Intelligent Network Platform integrates both the Content Inspection Engine and the Accelerated Application Engine along with other key software components to allow the design of high-performance intelligent network applications in a consolidated management and data plane system. The Intelligent Network Platform can be used in its entirety or in a modular fashion, in many cases, with companies interchanging and extending individual components with their existing in-house technologies. Key components of the platform are shown in Figures 2 and 3.
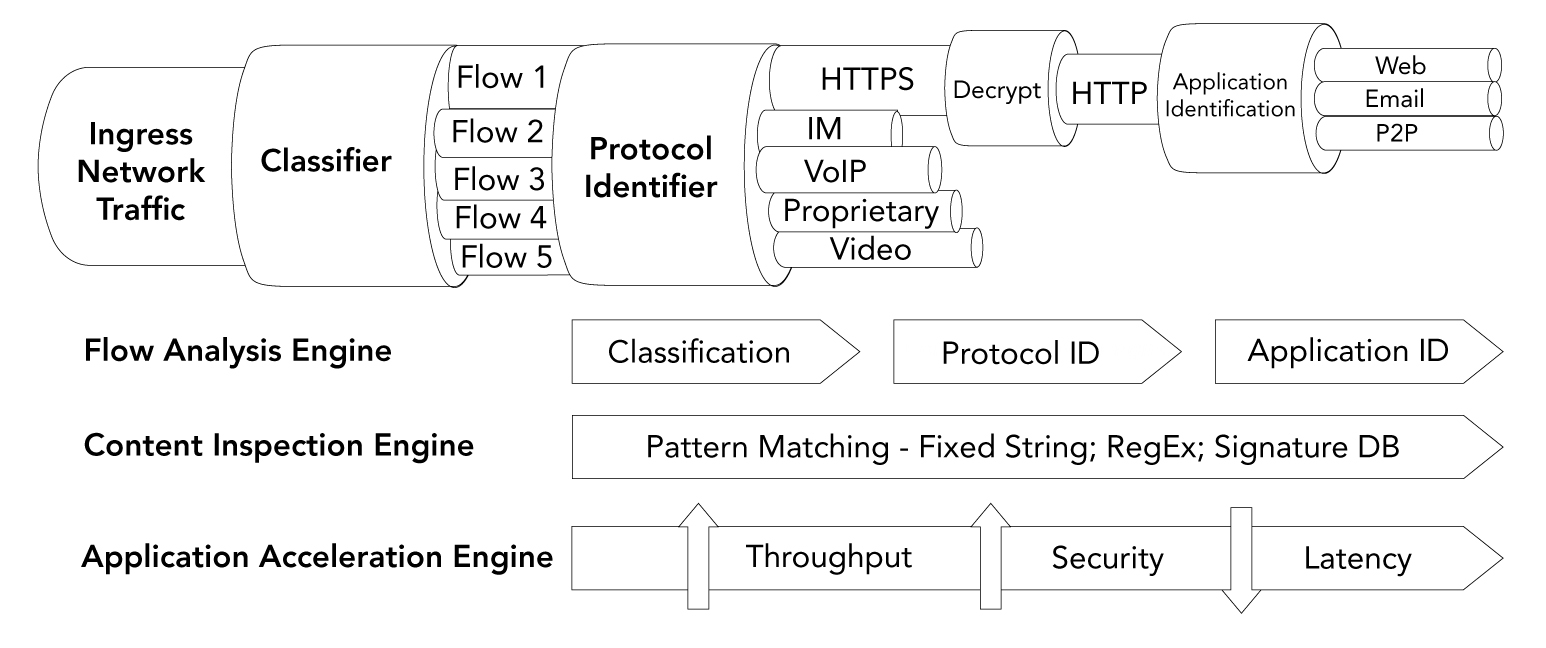
Figure 3: Network acceleration, deep packet inspection and packet identification in one system
In addition to the Content Inspection Engine and Application Acceleration Engine, the complete platform also includes a Flow Analysis Engine, which offers complete visibility into network traffic in real time, including flow classification, protocol and application identification, and metadata extraction. Also included is the Intel Data Plane Development Kit (Intel DPDK) library, plus optimisations for carrier grade Wind River Linux, including the flexibility to support other Linux distributions. The platform enables the acceleration of Linux-based applications up to three times faster without the need to modify code in existing applications. Even greater performance can be achieved of up to five times faster if an application is specifically ported and optimised for the platform.
Key applications for the platform include: cloud radio-access networks; intrusion detection and prevention applications, media gateways; mobile access, edge and core; next-generation firewalls; server acceleration and offload; and virtual private networks (VPNs).
In summary, Wind River Intelligent Network Platform is a software platform for the development of sophisticated network equipment that can accelerate and secure the flood of traffic for current and future networks. Additionally, the high-performance of multi-core processing technology from Intel and others have helped realise the possibilities for service providers and network equipment suppliers to use leading-edge software-based DPI solutions to accelerate, analyse and secure applications, in turn enabling increasingly intelligent solutions for mobile, fixed and enterprise networks.










