Securing the Internet of Things
Traditional network and endpoint protection mechanisms are struggling today to protect our corporate IT infrastructure and computers. Adding the projected billions of nodes that will constitute the Internet of Things exacerbate the problem dramatically. By John Blevins, Director of Product Marketing, LynuxWorks.
The advantage that the embedded industry has over the traditional computer world is that devices are generally being built for a specific purpose and so, as part of the design, security and protection can often be a primary consideration. However, adding security of any form to a resource-constrained device that isn’t secure by design is almost impossible.
Providers of the traditional embedded software platform — the real-time operating system — are in a prime position to address this need by stepping up and offering the security functionality developers need to protect connected embedded devices and allow them to be designed secure.
NSA’s ‘Protection Profile for Single-level Operating Systems in Environments Requiring Medium Robustness’ (SLOSPP) specifies the security requirements for commercial-off-the-shelf (COTS) general-purpose operating systems in networked environments that contain sensitive information. LynuxWorks LynxOS 7.0 is amongst the first to implement these standards, allowing developers to embed military-grade security directly into their devices.
Security features include discretionary access control, audit, roles and capabilities, identification and authentication, cryptography, quotas, self-test, residual information protection, and local trusted path; features that can help protect networked embedded devices from malicious attacks.
Discretionary Access Controls (DAC) are a means of restricting access to objects (such as files, applications, directories, and devices), based on the identity of the user or group to which they belong. LynxOS implements DAC using Access Control Lists (ACL) as defined by the Posix.1e standard. ACLs provide for much finer grain control over who can access an object as compared to the traditional UNIX ‘user/group/others’ security implementations. ACLs allow authorised users to specify which resources may be accessed by specific users and groups of users. Essentially, DAC gives the networked device the ability to carefully control who can access and execute files and data on the device.
Audit facilities allow an embedded device to capture significant system events and perform security monitoring of these events. LynxOS 7.0 supports fine-grained event auditing with events like login, logout, object accesses, and administrative tasks, which can all be logged to an audit trail. The audit trail contains invaluable information that can be used to: review security-critical events; discover attempts to bypass security mechanisms; track usage of privileges by users; provide a deterrent against attempted attacks since audit logging captures intrusion, and; perform forensic analysis
LynxOS 7.0 audit records contain information such as the audit event, the user that caused the event, and success or failure of the event. It also provides utilities to monitor the live audit events as they are occurring and to analyse the audit records written to the audit trail, helping to make connected devices much more secure.
Better than Unix
Roles and capabilities provide finer grain privilege levels for users over the traditional UNIX model. Historically, in UNIX and similar systems, privilege to perform administrative tasks is reserved to the root user, who has complete privilege to see or modify the entire system, whether or not those privileges were required by the original task at hand. Normal users, on the other hand, had no administrative privileges whatsoever. A normal user could do only what was allowed based on his or her user ID and group ID.
In general, the all-encompassing privileges of root makes it susceptible to abuse, whether unintended or malevolent. This problem is resolved in POSIX.1e by decomposing the root privileges into a set of fine-grained privileges or capabilities. The idea is that instead of having an all-powerful root user, one can create multiple administrative ‘roles’, each with a subset of privileges (called ‘capabilities’) specific to the task at hand. For example, one might create a ‘netadm’ role and only give it the capabilities related to manipulating the network (CAP_NET_ADMIN). One might create a second role called ‘auditadm’ and assign to it the capabilities of controlling the Audit logs (CAP_AUDIT_CONTROL) and writing to those logs (CAP_AUDIT_WRITE).
Embedded devices that implement distinct roles, each with limited capabilities, will be more secure against attacks which target and compromise a specific ‘user’ account on the system.
Identification and authentication refers to the process whereby a device on the network recognises a valid user’s identity and can verify (authenticate) the claimed identity of the user. LynxOS 7.0 identifies users with the traditional POSIX.1 user id/group id model, where a user has a unique user id and is a member of one or more groups.
A strong identification and authorisation mechanism such as that in LynxOS 7.0 significantly reduces the risk of unauthorised users gaining access to embedded devices.
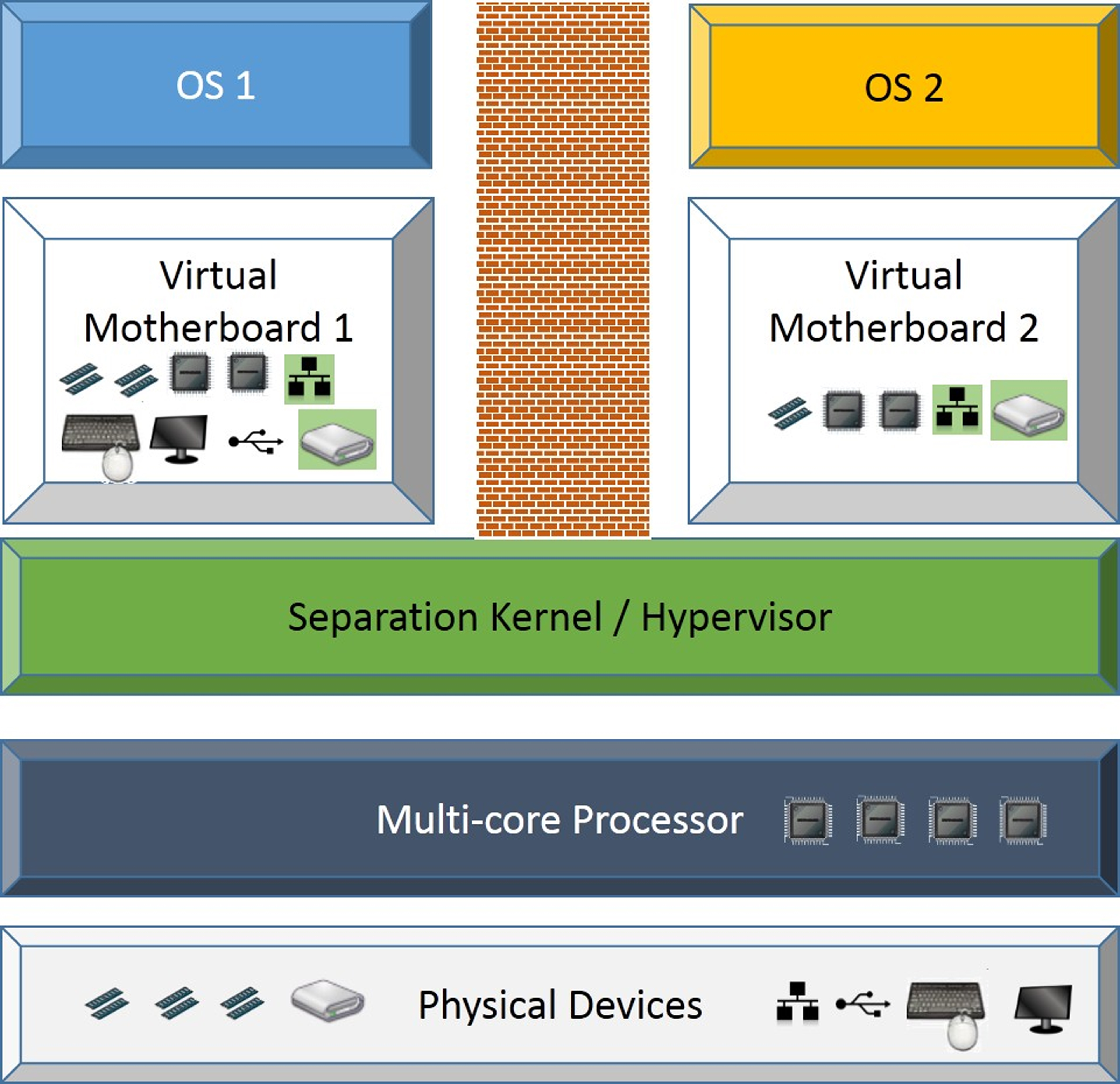
Figure 1: Type-0 hypervisor offering two secure virtual motherboards to guest operating systems
Cryptography provides techniques for secure communication in the presence of potential adversaries. Cyrptographic software uses sophisticated algorithms to turn plaintext data into nonsensical strings and vice versa based on encryption keys (public, private) and digital signatures.
LynxOS 7.0 implements the FIPS 140-2 certified crypto algorithms and random number generators based on the certified OpenSSL and OpenSSH libraries. These libraries provide powerful open standard security protocols for the Secure Sockets Layer (SSL), Transport Layer Security (TLS), and a full strength cryptography package. Embedded devices on the network can take advantage of the FIPS 140-2 certified crypto algorithms to protect sensitive data and passwords.
Memory management
Quotas are implemented to protect the device from running out of disk, memory, or CPU bandwidth. As an example, if a denial of service attack is made against the system with the intent of over-utilising the CPU, an unprotected device could essentially appear to freeze up. By being able to set limits on the amount of critical resources — such as the CPU — a task is able to consume, the overall system is protected from such an attack. Likewise, if a process tries to allocate memory or disk resources and the usage of the user or group exceeds the quota then an error will be returned and the allocation will fail.
Self-Test provides the ability to run a set of tests during the device’s initial start-up, periodically during normal operation, or at the request of an authorised administrator to demonstrate the correct operation of the device. LynxOS self-tests are designed to provide confidence that the devices memory and file systems are in the expected state.
Residual information protection is a feature that insures that whenever a resource is allocated or freed, the content of the resource can be made unavailable to other processes. LynxOS 7.0 makes user memory and file system data unavailable to others when it is freed resulting in a more secure system. Whenever a file system object is removed, all the blocks allocated to that file system object will be filled with zeros. LynxOS can be configured to fill memory allocated or freed by a process with zeros.
Trusted path is a mechanism that provides confidence that the user is communicating with what the user intended to communicate with, ensuring that attackers can’t intercept or modify whatever information is being communicated. LynxOS 7.0 uses a simple and elegant mechanism called Secure Attention Key Sequence to provide a trusted path because normal programs can’t intercept this key pattern; this approach creates a trusted path between the user and the LynxOS computing base. LynxOS also provides a modular framework called Trusted Menu Manager (TMM) for all trusted operations. Trusted operations such as user login, role login and password change operations can be performed from this menu, as well as screen locking/unlocking.
The trusted path mechanisms combine to ensure that a user supplying sensitive data, such as login information, will not have to worry about their login information being stolen by spyware programs.
It is easy to see that with these new powerful RTOS security features available to embedded developers they can design their systems to be more secure before they are connected to the internet. Once the applications are secured, developers can take advantage of LynxOS’s networking support for both long haul networks using TCP/IPV4, IPV6, 2G/3G/4G cellular, and WiMax communication stacks as well as short-haul networks common with M2M applications such as 802.11 Wi-Fi, ZigBee wireless mesh and Bluetooth.
For systems that require the use of a more general purpose OS, such as Windows or Android, for user familiarity, security becomes more difficult to design into the operating system itself and other protection or isolation mechanisms need to be used to help protect against cyber attacks.
Virtualisation
There is another technology available today from LynuxWorks called LynxSecure which allows embedded developers to build security into their systems, regardless of which operating system is used. Originally designed and developed to meet the exacting security needs of the DoD, a separation kernel is a technology that provides isolation of devices and memory on a microprocessor based system. It is particularly well suited to embedded devices as it is typically a very small and efficient kernel implementation offering real time properties as well as isolation. In DoD systems the separation kernel is used to help provide domain isolation for applications running at different security levels on a single hardware system and protected domains from seeing each other’s data, network and applications.
Adding virtualisation to an embedded system is now particularly interesting as more embedded processors contain two or more cores. Using virtualisation is a good way of segmenting a multi-core system in an efficient way and offers consolidation of multiple physical systems onto a single multi-core system. A flexible separation kernel/hypervisor solution will allow the embedded developer to look at the requirements of each guest OS, and allocate the appropriate number of processors. This could involve sharing processors across multiple OSes, dedicating a single core to a single OS, or allowing OSes that support symmetric multi-processing to access multiple cores.
As embedded systems use more traditional computer OSes and then link to the open internet, they are every bit as vulnerable to stealthy cyber threats as our normal computers. However, unlike our normal computers, these embedded devices could be controlling our critical infrastructure and when infected could pose a dramatic security breach, even affecting nation states. The latest super stealth cyber weapons include rootkits and bootkits that infect the system below the OS, residing on hard disks, in devices or in memory, waiting for instructions from a command and control centre communicating over the internet before actually starting the attack. Traditional network and endpoint protections are quite poor at detecting them and general purpose operating systems are very susceptible to them, hence connected embedded systems are vulnerable to them. The LynxSecure separation kernel/hypervisor is now armed with a rootkit detection feature that has been designed to detect and alert when the rootkit has entered the system and is looking for a place to hide itself.
The propagation of connected embedded systems, as predicted as part of the Internet of Things is opening up a potential security hole for cyber criminals and cyber terrorists to take advantage of. Embedded developers now have new military-grade tools available to design security into their devices at the RTOS level as well as by using a secure separation kernel/hypervisor. For smart devices these threats can be mitigated and detected long before the attack has really started.
Author profile: John Blevins is the Director of Product Marketing at LynuxWorks. He has over 25 years of software development experience in the embedded industry working primarily on software compilers, debuggers, IDEs and related tools. He can be reached at jb@lnxw.com.










