Increasingly connected world needs greater security
As the connected world increasingly becomes a reality in industrial set-ups, there is danger they are becoming more vulnerable to attack. Steve Rogerson looks at the risks for ES Design magazine.
The predictions for how many connected devices there will be in the so-called Internet of Things are varied but what everyone agrees is that the numbers will be large. One of the major growth areas is predicted to be the industrial environment where programmable controllers will now be in charge of large sensor networks. While that is, to a degree, already the case today, especially in the more automated factories, its spread is expected to be immense. Even existing networks in automated factories will grow in complexity, with more intelligence at the edge.
Sensors and small MCUs at the end points will be collecting and processing data before it is passed to data centres and the cloud. The ability to monitor and control factories remotely will also increase. While this has many potential benefits to the efficiency and productivity of these workplaces, it also brings the possibility of them being opened up to hackers, competitors and even terrorists. This means a major shift in the way these companies deal with security has to happen, moving from preventing unauthorised physical access – still important – to stopping electronic access on their internal networks.
“There is a challenge here to make sure there is security from end to end,” said Tim Summers, Operations Manager, Freescale. Will Keegan, Technical Director, LynuxWorks, added: “They will be using more intelligent devices on a larger network, so there will be more points of entry that can be exploited. Once you just needed to prevent physical access, but when you have wireless access and nodes with multiple stacks, there are many ways to enter the network for people who know how to do that.” And Roger Highton, Product Line Manager, Eaton’s MTL Instruments subsidiary, said: “Ten years ago, the intelligence was more in the controller. Now, with the Internet of Things, we are seeing flow valves and the like connected over Ethernet. The volume of connections is greater so the threat is greater.”
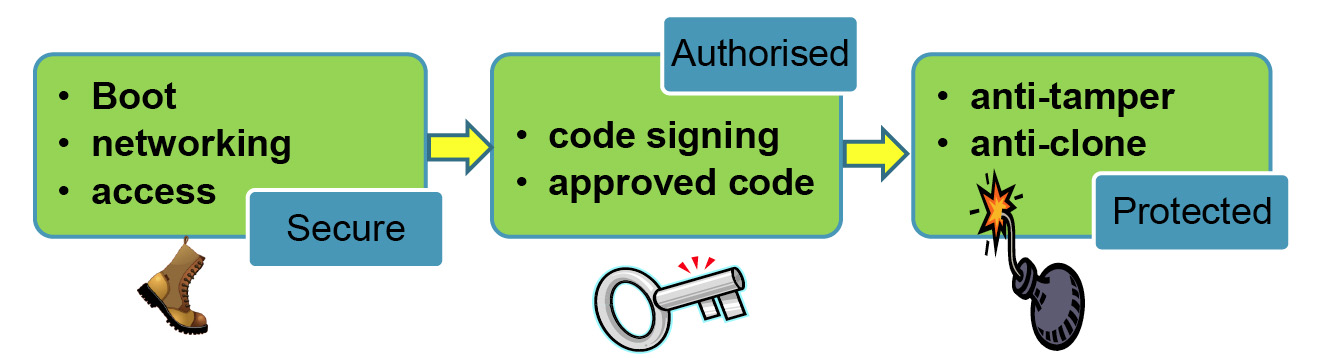
Stages for secure communications
To see how much damage a malicious intruder could cause, consider a smart grid. The idea is to keep electricity consumption and generation well balanced. If the grid was fed false information, the effects could be catastrophic. “You could cause an explosion or a massive blackout,” said Summers. “You could also get a sabotage attack on a factory that has sensors controlling the manufacturing flow. If someone gets to the sensor node and injects a virus, it could upset the whole balance of the factory.”
Cost
The downside is that any security has to be reasonable priced. Putting large amounts of security on all the edge devices would make the expected growth of the IoT too expensive. “It could put a brake on the whole thing,” said Summers. “You need to scale the security from the high-end products down to $3 to $4 MCU designs. It also has to be done in a way that does not use massive amounts of CPU power.” But Keegan thinks the cost factor will cause some companies to be lax with security. “Security has to cost something, and usually a lot,” he said. “In some cases cost will win out and we will see a lot of really bad implementations. These will open people up to attacks. But it can be hard to work out what is worth paying for. The cost will come down, but the best is to adopt really efficient ways to build quality stuff.” He said the simpler approach here was often better. Rather than, say, building a perfect network stack that will cost a lot of money, go for one that runs on Linux and is free.
“Focus your resources on building a system that is much simpler,” he said. “Try not to spend too much time on the really complex stuff as that will cost a lot.” There also needs to be a judgement call on the level of security needed versus the damage that could be caused. Some low risk applications may need no security at all as there is little for a malicious hacker to do. A good example could be environmental monitoring for research purposes.
“In some cases, it doesn’t matter if people get in,” said Summers. “But if the end points are supplying spurious data you might want some pattern recognition technology at the gateway to spot suspect data. There might be no need to secure all the end points.” On the other hand, some need to take security very seriously. “The people who own the refineries and chemical plants need to do their homework,” said Keegan. “They have to look at how the networks are built, what operating system they are using, how they are integrated and so on.”
A typical factory set up would therefore have different levels of security – low or no level on the individual sensors and edge MCUs, a medium level on the gateway or factory controller and higher level at the data centre. The low level security could involve some kind of key exchange to verify that any connection is valid before a communications pipe is established.
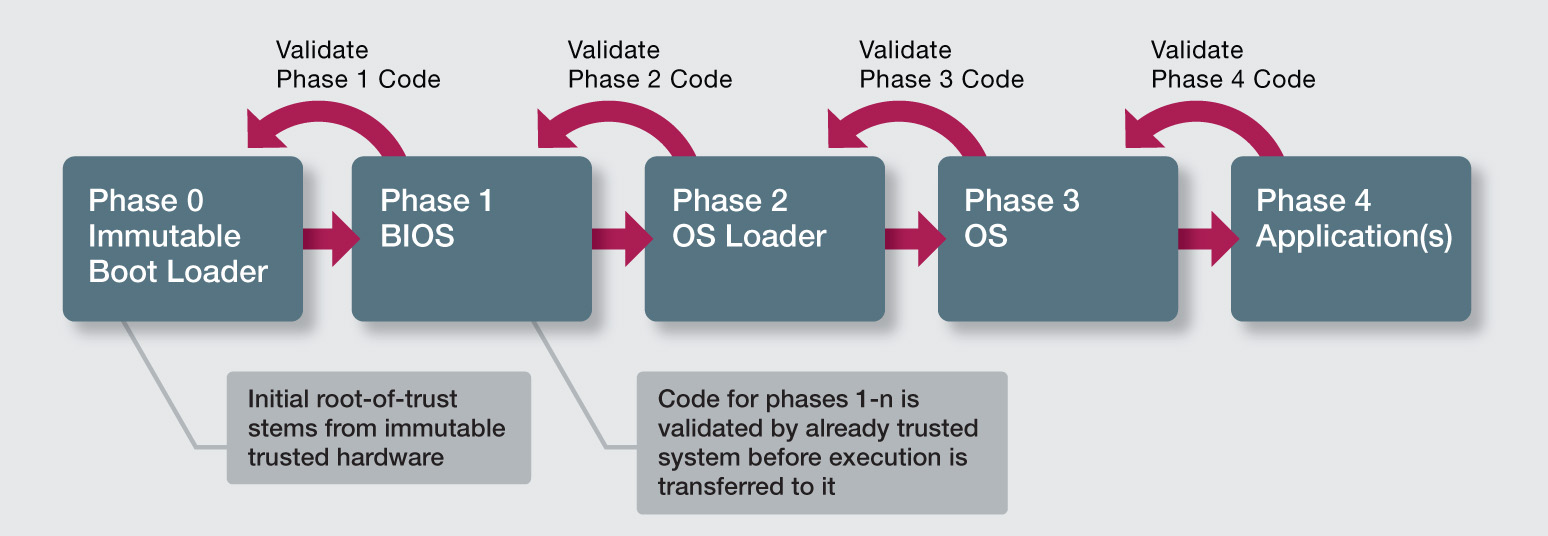
How a secure boot system could work
“I don’t think the little scanning sensors will need a whole lot of security at this point in time,” said Tim Morin, Director, Product Line Marketing, Microsemi. “It is the network where the problem is today. The problem is in the hubs and programmable logic controllers. They are very easy to attack. Over time, you might see the MCUs in the sensor system becoming more secure, but that is not where the threat is yet and it would cost too much. We need to plug the big holes first and worry about the little holes later.”
Another aspect of this is secure boot. When a device is powered up, it is important to make sure that happens from valid code. Tampering with code in this way has caused problems in the past in the mobile phone industry where it has been used to affect revenues. Similarly, rootkits can be installed that allow hackers continual access to a computer.
“You need a key that is programmed in when the board is made,” said Summers. “The device can then check the signature of the code. If the key matches, it will boot.” The third aspect is to make sure a device cannot be tampered with or cloned. Again in the cellular industry, there have been examples where people have reverse engineered base stations and tampered with the code using debugging equipment. Thus, anti-tampering security could work by only allowing debugging tools with certain codes access. If an unrecognised tool attempts to make contact, the device could blow fuses or power down.
Remote access
A particular vulnerability is where a factory’s network can be accessed remotely so, say, the plant controller can make changes and monitor what is happening when he or she is away from the factory. “That opens a channel that other people can get into,” said Keegan. “You need to look at how to separate the different domains and put blocks between them. You need to look at what is guarding this and how reliable it is. You cannot take remote access lightly.”
Whatever security is installed, an attack can still happen and the system must be designed to know how to cope with this if it gets past the initial security. In the IT world, the answer was often just to shut everything down, but that cannot happen in many factories where the shut down has to happen in a controlled way to prevent accidents.
“In a controller system, the last thing you want is to block all traffic,” said Highton. “The shutdown has to be controlled. So the way this is executed is different from an IT system.” Morin believes security is often seen as an add on rather than something that is being designed in, and thus he thinks education is needed to make system designers take security more seriously: “Engineers are not security aware today,” he said. “If you put 100 engineers in a room, they will all know about C but when you ask about security only two or three will raise their hands. Design engineers need to understand how to design security into a system.”
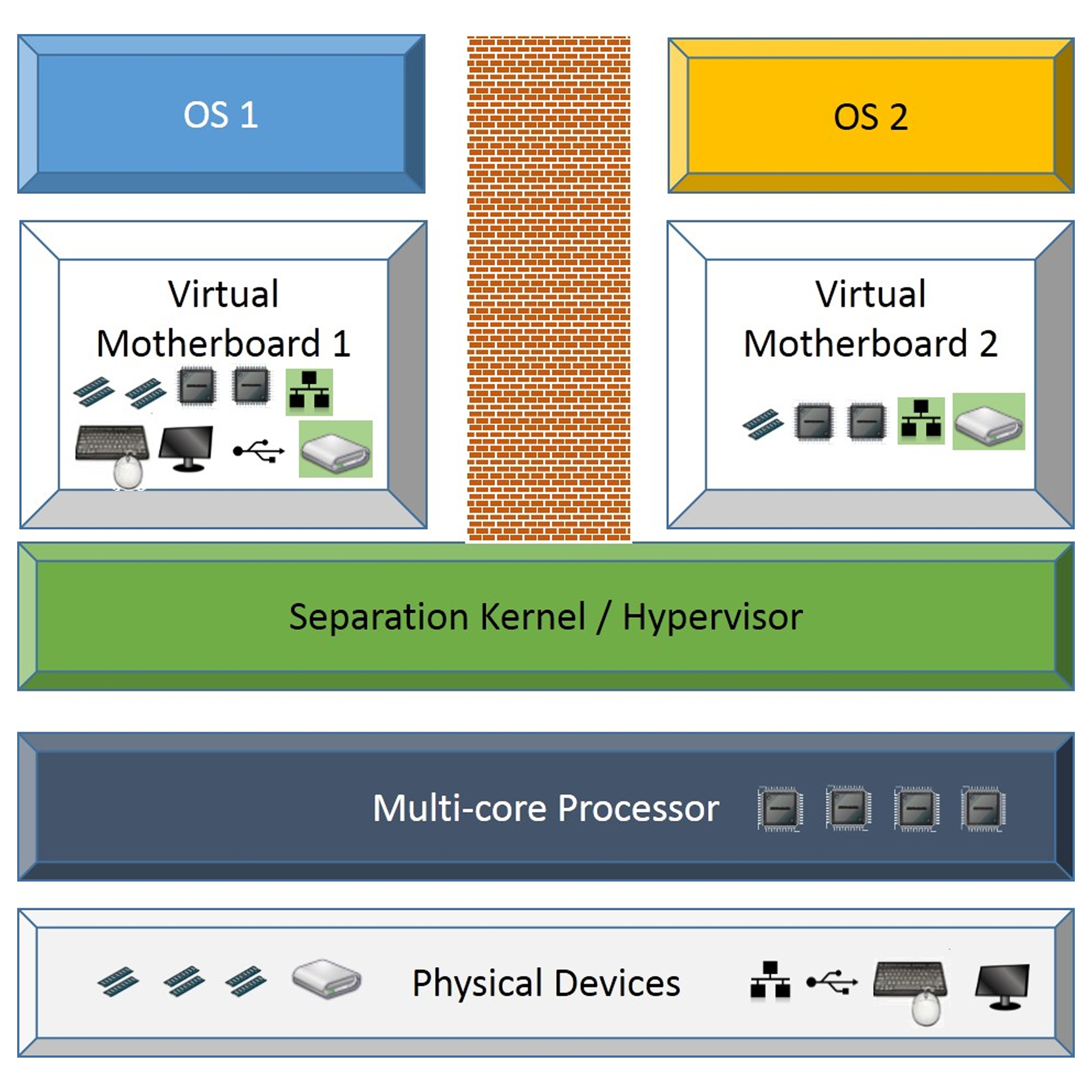
Keeping different parts of a system apart can increase security
Keegan added: “One thing that could be done would be to adopt better coding and design practices. Regulation doesn’t improve quality but does force people to look at their work.”
Morin said the ideal would be a system where every chip on a board authenticates each other before the board powers up. “That is the ultimate, but we are a long way away from that,” he said. “That is a multi-layered approach to make sure the system powers up securely.”










