Biometric signature authentication guards EMR access
Every hospital administrator, CFO and medical group CEO must comply with recent regulations from federal HIPAA and HITECH legislation, or risk forfeiting funds previously received from the Center for Medicare and Medicaid Services. Great emphasis is being placed on physicians and paramedical staff, as well as record keeping and insurance-billing departments, actually using the EMRs (Electronic Medical Records) as required.
There have been recent introductions of biometric signature authorisation systems that allow users to effortlessly manage EMRs on their existing smartphone, tablet or desktop. At the same time, the latest iterations of biometric signature authorisation meet the 'meaningful' needs of the medical organisation by abiding by the letter of the law through gate-access specificity approaching 100%. The fact that the these new systems reside in the cloud outside of the company‘s business system, and require absolutely no additional cash-outlays for hardware, mark them as a cost-effective option for compliance.
Play or Pay
By now, the medical community understands the consequences of failing to employ meaningful use and safeguard the access to personal health information. Federal law (42 USC § 1320d-5) enhances this message by imposing stiff penalties that start at a minimum $100 per violation and go up to $50,000 per violation with an annual maximum of $1.5m.
Access portals act as watchful sentinels to any EMR system. When they fail, the entire system is compromised. In March, 2012, hackers managed to steal the medical records, including social security numbers, of 280,000 patients seen by the Utah state Health Department. The breach occurred at the password authentication level.
Jeff Maynard, CEO, Biometric Signature ID, commented: “Most of the administrators I speak to tell me that their biggest fear is having their organisation’s EHR system compromised. The stakes have been upped by the HIPAA and HITECH acts. When you allow unauthorised access, then you can be held personally liable for the fines, as well as the organisation.”
More than 80 clients and nearly 2m users in approximately 60 countries (including all 50 U.S. states) currently utilise the company’s biosignature software.
To avoid breaches to the system, and stop haemorrhaging at the bottom line, healthcare portals must meet several criteria. These include:
- Ensure that first time users are who they say they are;
- Secure access by physicians, nurses, etc. to clinical applications that contain patient data;
- Secure access by payees and other third parties; and
- Secure any session both before and after login.
CFR 45, Section 170.314(d)(1) summarises it as: the system must verify against a unique identifier (such as a username or number) that a person seeking access to EHR is the one claimed.
Finding a secure solution
A number of identification-checking modalities currently exist, falling into three basic categories:
- Something only (presumably) the user knows, such as a PIN or password;
- An item the user has in his or her possession, such as a proximity card, flash drive or a token that provides random authentication codes; and
- Biometrics, something physically unique to the individual. This is where the challenge begins.
The failure of relying on something the user knows has become all too apparent. Cybercriminals have repeatedly proven the ease of cracking passwords and PINs. Secondly, requiring a user to possess a verification tool, like a flash drive or proximity, entails the cost of purchasing, producing and distributing the necessary hardware. Of even greater concern, such devices do not necessarily authenticate the individual. They only verify that a person has possession of the device or card.
Which leaves biometrics. Examples include fingerprints, iris scans, facial recognition, DNA sequencing and vein scanning. While these may offer near-absolute verification, this type of identification requires a sophisticated, expensive, hardware device to capture and interpret the biometric patterns.
Eliminating the need for a hospital to purchase a scanning device for its medical staff and other employees, Apple has brought fingerprint scanning to the smartphone in the form of its Touch ID application; but this is not without its flaws.
“Fingerprint scanning seems convenient, but will lead to many case of blocked access, especially in a clinical environment. Antibacterial hand creams, powder from latex gloves, etc. will dirty the screen and reduce accuracy down to as low as twenty or thirty percent. If authorised users can’t access the system, they will rebel and refuse to use it,” said Maynard.
As a subset of biometric physical qualities, dynamic (behavioural) biometrics offers the possibility of more accurate identification with less false negatives. Among the already proven types is 'finger writing', a type of gesture recognition verification.
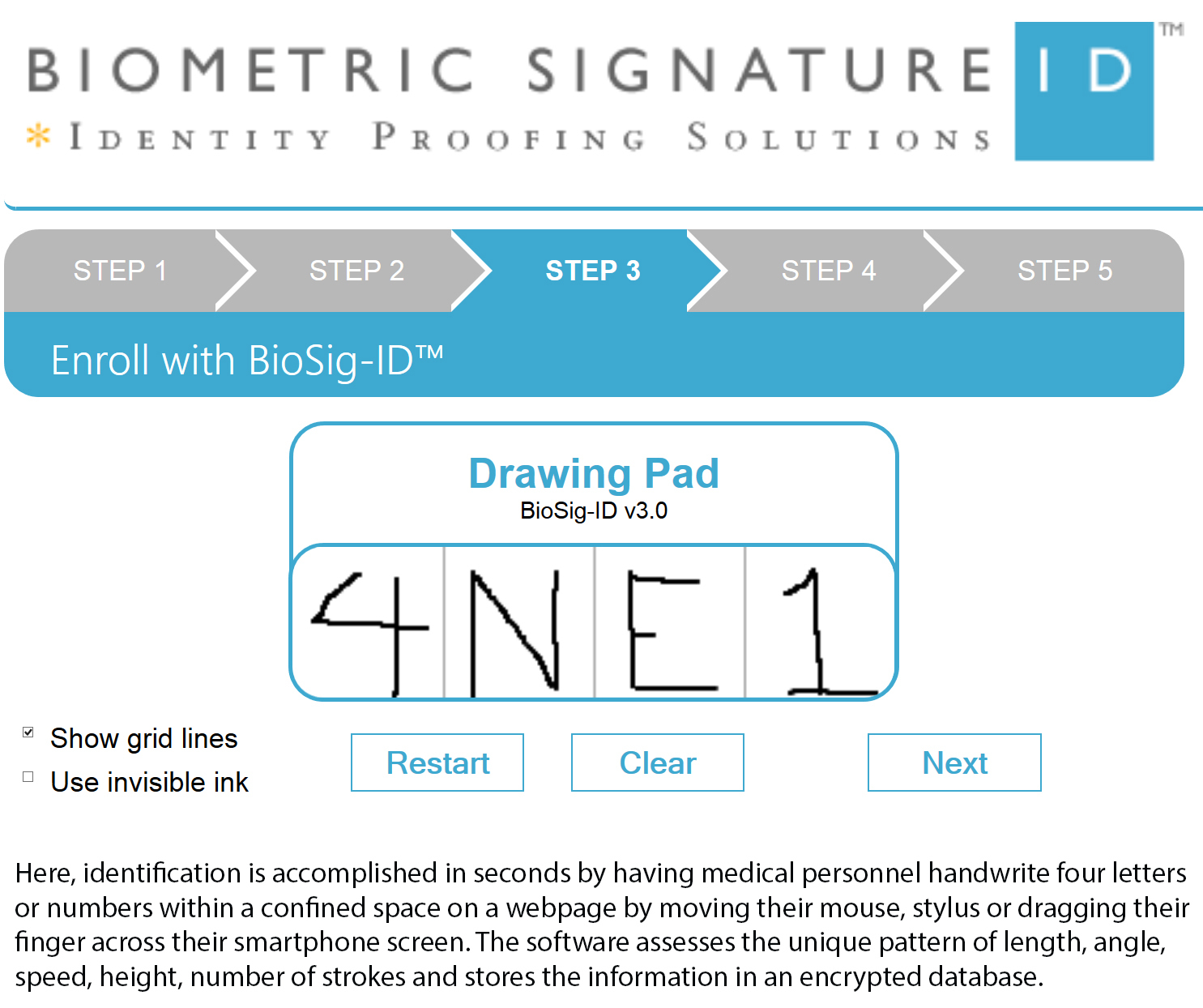
Here, identification is accomplished in seconds by having medical personnel handwrite four letters or numbers within a confined space on a webpage by moving their mouse, stylus or dragging their finger across their smartphone screen. The software assesses the unique pattern of length, angle, speed, height, number of strokes and stores the information in an encrypted database. This data is compared to patterns collected by the user’s subsequent logins, confirming that the person who registered is the same person trying to access the account.
In independent testing by the Tolly Group, the BioSig-ID gesture recognition system was found to be 27 times more accurate than keystroke analysis reported in earlier evaluations. Observed confidence ratings at 99.97% meant that the false positive level of this particular software was three times better than guidelines put out by National Institute of Standards and Technology.
But will they use it?
Accuracy aside, the payoff to such systems is its ready adoption by medical staff.
In fact, its very accuracy helps ensure acceptance because of the lack of false negatives. Additionally, since the reader is virtual and resides in the cloud, even users who do not have a smartphone can access it from any tablet or desktop computer, making it instantly and universally available.
It is all about the user experience and flexibility according to Maynard. Experience surveys report a 98% positive rating from users with many even reporting that it’s ‘fun’.
Maynard explains: “Taking it one step further, in terms of timesaving and convenience, with our mobile app a user need only acquire authentication via his or her biosignature once. Upon which the system can be set up to respond with a RSA style key code, QR code or even NFCs that land in their smartphone. From that point on the user can employ that code as a ‘key’ to access the facility’s EHR. The duration of the key’s access rights is configurable from groups to individuals.”
Since one of the biggest concerns today is how to manage and secure personal devices, BioTect-ID - using BioSig-ID biometrics - was created to lock down mobile devices, tablets and workstations to further prevent un-authorised access and data breaches.
Through easy and convenient, yet secure, access to medical records, applications, and even physical corridors, physicians and staff can accomplish their assigned tasks without fear of violating the law and incurring risk to the facility.
Recognising these advantages, leading healthcare and enterprise companies like Epic and Ping Identity have already moved to integrate with Biometric Signature ID.
Covering future contingencies
New rules issued last year by the U.S. Department of Health and Human Services further tighten the requirements for protecting patient privacy and securing their health information.
The Federal Regulations/Interpretive Guidelines for Hospitals (482.24(c)(1)(i)) require that every entry in the health record should be authenticated and traceable to the author of the entry. Hence, any authentication system must incorporate some method of tracking.
“A good biosignature system can provide an audit trail including the time, date, physical location, history and even the ISP/IP address of a user who signs in for any medical record or through a portal,” adds Maynard. “Through continuous data mining we have developed risk scoring algorithms that uncover fraudulent activity. Examples include, comparing the history of IP address, ISP’s, accuracy levels, password resets, validation attempts and more data that point to atypical behaviours. We can set up certain alerts and bring this information to the attention of the medical institution.”
Industry accepted application program interface standards like SAML 2.0, SSO-IO communicate with the business systems of the medical enterprise to allow seamless exchange of such tracking information.
The ability to provide evidence of all the events surrounding the authentication activity not only provides a powerful tool to combat fraud, but also ensures compliance with evolving regulations that portend to mandate even stricter standards of identity authorisation within the healthcare industry. Leading healthcare and enterprise companies like Epic and Ping Identity have already seen the handwriting on the wall and have integrated with Biometric Signature ID.










