No security compromising when virtualising control applications
Virtualisation can bring a wide variety of benefits to industrial control applications without compromising on the level of security delivered by traditional physical infrastructure, as long as you have selected the right software platform.
Guest blog by Charlie Ashton.
Moreover, virtualisation will enhance your system-level security by enabling dynamic updates in response to emerging threats.
In industries such as energy, manufacturing, healthcare and smart buildings, there are countless examples of companies relying on industrial control systems installed twenty or thirty years ago. Increasingly, though, these legacy deployments present major business challenges such as: increasing operational expenses due to high maintenance and replacement costs; a dwindling pool of skilled technicians; limited flexibility resulting from sole-sourced solutions with proprietary programming models; slow product lifecycles out of step with fast-moving IT and mobile technologies; out-dated box-level security features with no provision for end-to-end threat protection or dynamic updates.
To address these challenges, innovative companies are leveraging virtualisation in order to slash their operational costs by deploying secure, robust, flexible software-based solutions as alternatives to legacy, fixed-function hardware.
With virtualisation, Level 1 through Level 3 control functions are consolidated onto standard IT-class servers for significant CAPEX and OPEX savings, resulting in software-based digital controllers, PLCs, DCSs, SCADA software, HMIs, historians and applications.
Updating software is significantly lower cost than replacing physical equipment. At the same time, companies can differentiate through software solutions while avoiding the cost, risk and down-time of removing and replacing proprietary hardware and software.
As companies evaluate the benefits of introducing virtualisation into their systems, security is a critical factor and there are typically two aspects to consider. On one hand, software-based solutions offer end-to-end security both for the network and for the control functions, permitting dynamic updates in response to emerging threats while leveraging software firewalls, VPNs and Intrusion Prevention Systems from leading IT software vendors.
On the other hand, hardware-based security functions are well understood and have a proven track record within critical infrastructure applications, so it’s important to ensure that that the adoption of virtualisation does not in any way compromise the level of security compared to what’s available in hardware solutions.
The Wind River Titanium Control platform addresses this need, ensuring that virtualised control functions achieve a level of security at least as high as that provided by the latest hardware technologies.
This post focuses on support for the Trusted Platform Module (TPM) function within Titanium Control. Subsequent posts will address additional security features in the platform, also summarised in the product overview.
Summarising the background to this, TPM is an International standard, based on the Intel Trusted Execution Technology (Intel TXT) specification, for a secure crypto processor, originally viewed as a dedicated microcontroller designed to secure hardware by integrating cryptographic data into devices. The TPM specification was written by the Trusted Computing Group (TCG) consortium and standardised in 2009, with the latest version being TPM 2.0.
TPM offers facilities to provide measurements of software and platform components so that system software as well as local and remote management applications may use those measurements to make trust decisions.
TPM’s support of remote attestation creates a nearly unforgivable hash key summary of the hardware-plus-software configuration. TPM also offers facilities for the secure generation of cryptographic keys, binding which encrypts data using a TPM key and sealing which encrypts data in a similar manner to binding but also specifies the state in which TPM must be in order for the data to be decrypted (unsealed) and a random number generator.
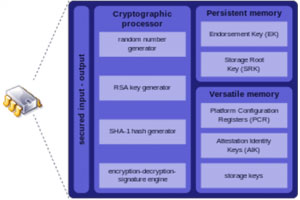 Software uses TPM to authenticate hardware devices. Since each TPM chip has a unique and secret RSA key burned in during manufacturing, it is capable of performing platform authentication.
Software uses TPM to authenticate hardware devices. Since each TPM chip has a unique and secret RSA key burned in during manufacturing, it is capable of performing platform authentication.
One of the key benefits of virtualisation in industrial control applications is that it enables the software-based control functions to run on generic server platforms located on-premise, either in a stand-alone configuration or a mini data centre.
In either case, customers expect to be able to deploy industry-standard servers that may not include hardware TPM. Virtualisation also allows Virtual Machines (VMs) to be dynamically migrated from one physical server to another, whether to eliminate down-time during software updates, to recover automatically from platform failures or to adjust resource utilisation in response to changing workloads. Binding a VM to a physical TPM severely limits the scenarios under which dynamic VM migration is possible.
To address these challenges, the Titanium Control platform has introduced an industry-leading virtual TPM (vTPM) feature. The vTPM comprises a complete software-based implementation of TPM 2.0. The vTPM device is instantiated on the trusted/secure Titanium Control host (encrypted).
This enables Titanium Control to manage the vTPM device and its non-volatile data securely through the VM’s lifecycle, including migrating it along with the relevant VM. The vTPM device is configured exactly the same as a physical TPM and no changes are required to the application itself, which behaves exactly as if it had booted from a physical TPM.
For industrial control applications, it is critical to ensure an end-to-end boot process that is fully secure. With Titanium Control, vTPM is a crucial element of that boot process, which runs in the Unified Extensible Firmware Interface (UEFI) mode.
The vTPM feature in Titanium Control enables Wind River’s customers to achieve the full range of benefits from virtualised industrial control functions without compromising on the security that is an absolute requirement for critical infrastructure.
This post has only scratched the surface of the features in Titanium Control, all designed to streamline the deployment and operation of virtualised industrial control applications.
To find out more visit here.










