Channels of communication
Securing M2M communications using a physical unclonable function. By G. Richard Newell, Senior Principal Product Architect, SoC Group, Microsemi.
The number of devices capable of M2M communications is exploding in today’s world. An oft-quoted prediction by Cisco is that 50bn devices, many of them un-manned or operating autonomously, will be connected to the global internet by the year 2020; the so-called IoT. But M2M communication also utilises other types of networks: data transmitted over the cellular telephone infrastructure, personal area networks using Bluetooth or NFC, and more specialised networks such as for air traffic control, medical devices, and vehicles (V2x) for example. With the ascendance of multiple wireless communications protocols and public networks like the internet and cellular (vs. old-fashioned dedicated secure private lines), nearly all modern M2M traffic is vulnerable to malicious monitoring and modification and so must be secured against these attacks if the connected machines are to be used safely and with confidence.
There are a number of security services possible, two being confidentiality and authenticity. Confidentiality, typically achieved today by encryption, protects information from being learned by unauthorised viewers. Authenticity means that the message arrived intact with no undetected errors and comes from a known (trusted) source. Although confidentiality is the best known cryptographic service, authenticity is often the more important one in M2M communications. For example, in establishing a secure source of network time, it is not important to hide the payload (the correct time is not a secret); it is far more important to make sure that the time value being received hasn’t been tampered with and that it originated from a trusted source and not an adversary. This is consistent with the view taken in internet RFC 7384 on the security of time synchronisation using the IEEE 1588 precision time protocol standard.
I have a secret
In order to prove authenticity, the sender of a message must have a secret that when applied to a message can be verified by the recipient to prove the message comes from the true source. Cryptographically, there are two main avenues for doing this. In symmetric cryptography the sender and receiver machines share a secret key, often pre-placed in both devices and the messages are ‘tagged’ by the sender with a Message Authentication Code (MAC) computed from the message and the key that the receiver can verify using the identical key. This works adequately for virtual private networks with a small number of nodes. For larger networks symmetric schemes do not scale well: either the same key must be used by all the nodes, which presents an unacceptable security risk, or different keys must be used between each pair of devices, which is unwieldy because the number of keys can grow exponentially with the number of nodes. Asymmetric or ‘public key’ cryptography and hybrid schemes offer a better solution.
 SRAM start-up values are used to compute a private key made reliable with the aid of an 'activation code' saved during the enrollment phase.jpg)
a) SRAM start-up values are used to compute a private key made reliable with the aid of an 'activation code' saved during the enrollment phase.
b) From the private key, a public key is computed and certified by the component manufacturer, giving each component a verifiable, globally-unique, unclonable identity.
In asymmetric cryptography, the originator of a message has a private key that is known only to that node. The sender uses its private key to digitally sign outgoing messages. When a message is received, the authenticity can be proven by verifying the digital signature using the sender’s associated public key. Since only one device has to store the secret (private) key instead of two or more, security is improved. Any number of devices can use the public key, which can be transmitted along with the message and does not need to be confidential or stored permanently by the recipients. In case of a breach, only the affected device(s) need to be removed from the network and refitted with replacement key pairs. The overall system scales linearly with the number of nodes, a big improvement over symmetric key systems.
In a hybrid scheme, the private key is used to establish an ephemeral symmetric session key, and then a symmetric MAC tag is used to provide authentication. The overall effect is the same as the pure asymmetric key method except hybrid schemes are usually more computationally efficient. The session key may also be used as an encryption/decryption key to provide confidentiality.
There are a number of remaining issues: First, how to create and protect the private key used to establish the identity and create the digital signatures (or session keys) in the source machine, and second, how to distribute and ensure that the associated public key used to check those signatures is authentic.
The best private key for identifying a device is computed from something called a Physically Unclonable Function (PUF). A PUF is based on a physical characteristic that is created, effectively unintentionally, during a device’s manufacture that is unique for each copy of the device due to small uncontrollable random manufacturing variations. Even though these variations cannot be predetermined or controlled (i.e. cloned), if they can be measured with low enough noise and are stable enough, they can be used for a PUF. These measurements can be used to construct a private key specific to that particular device. A PUF is a ‘biometric’ of an inanimate device, analogous to a fingerprint or retina pattern of a human. Unique PUFs are created intrinsically in inanimate objects nominally manufactured from the same blueprints and processes just as unique fingerprints are created in human twins ‘manufactured’ from identical DNA. At some scales, perfect cloning is effectively impossible because small variations are unavoidable and PUFs use this fact to advantage.
Never the same twice
PUFs can have great security properties; arguably the best of any non-volatile key storage technology. Besides being unclonable - no two devices can be manufactured with the same properties, even if one tries - PUF-based keys can also be very difficult for an adversary to extract since the manufacturing variations exploited are often at the atomic scale. PUFs can be made in many forms, from tamper-resistant labels that go on pill bottles to electronic devices. IC PUFs can be based on memory elements, logic delays, resistance or other physical factors and are the most useful PUFs for M2M applications.
 SRAM bits are comprised of two nominally identical cross-coupled inverters.jpg)
a) SRAM bits are comprised of two nominally identical cross-coupled inverters.
b) Small random variations 'baked-in' during manufacturing cause each bit to have a preferred start-up state that is used to compute a secret key.
One of the best characterised and reliable type of memory PUF is an SRAM PUF, created on an integrated circuit such as a smartcard chip or an FPGA. It works by measuring the random start-up state of the bits in a block of SRAM. Each SRAM bit comprises two nominally equal cross-coupled inverters. But, since no two inverters are actually completely identical, the start-up state of each SRAM bit, when the power is first applied, will favour one state over the other, and consequently will start up in either the ‘one’ or ‘zero’ state, preferentially. This preference is largely ‘baked in’ during the manufacturing of the IC, independently for each bit.
For those bits where the inverters are exceptionally well balanced, thermal noise may overcome the baked-in preference and the bit will occasionally start-up in the opposite state from its normal state, but in most bits the random baked-in (static) preference is strong enough that it will overcome any dynamic noise. Temperature, lifetime and other environmental factors may also create noise. Noise is accounted for in the PUF design by using error correction techniques. When the PUF is first enrolled, a snap-shot is taken of the start-up values of the SRAM bits. An error-correction code, called an activation code (or sometimes helper data) is computed so that on all subsequent power-up cycles the noisy bits can be corrected and the values in the original snap-shot restored. That way, the same key is reconstructed at each turn-on. One nice thing about the SRAM PUF is that when power is off, the secret effectively disappears from the device: there is no known technology that can predict the start-up state of SRAM bits when the power is off. Another good security attribute is that if the activation code is zeroised (i.e. erased), the PUF secret key cannot be reconstructed no matter how thoroughly the device is subsequently analysed.
To give some idea of realistic values, an SRAM used to construct a single high-quality 256-bit cryptographic key may use 1-2kB of SRAM. Ideally each bit equally favours a one or a zero (i.e. 50:50 probability), and this preference is independent of all other bits. In this case, each bit is said to have 100% entropy. Due to small biases and correlations, real-world memory bits may only have 95% entropy. Dynamic noise, and environmental effects can create bit-flips compared to the originally enrolled memory image. In ideal turn-on to turn-on situations (e.g. constant temperature) the number of noisy bits may be in the 3 to 5% range. Over all conditions, including temperature and time, the noise may increase to 12 or 15%, still well within the range of the error correcting code (25% or more). The SRAM PUF is likely the best characterised and most reliable PUF technology, and can be designed to guarantee perfect key reconstruction over all environments and its full lifetime with errors as low as one per billion. This infrequent failure is detectable with high probability, and all that is usually required is to try again to get the correct key.
Having answered the first question, of how best to create and protect the private key used for creating digital signatures and establishing session keys, the second question remains about how to distribute and ensure the associated public keys are authentic.
Infrastructure
This calls for what is referred to as a Public Key Infrastructure (PKI). In a PKI, a Certificate Authority (CA) certifies all the approved devices that belong to the network by digitally signing their public keys using the CA’s own private key. The most common certificate format is defined by the X.509 standard. When a device transmits a digitally signed message (or establishes a session key) it can also send its X.509 public key certificate. The recipient can use the public key from the certificate to verify the digital signature on the message.
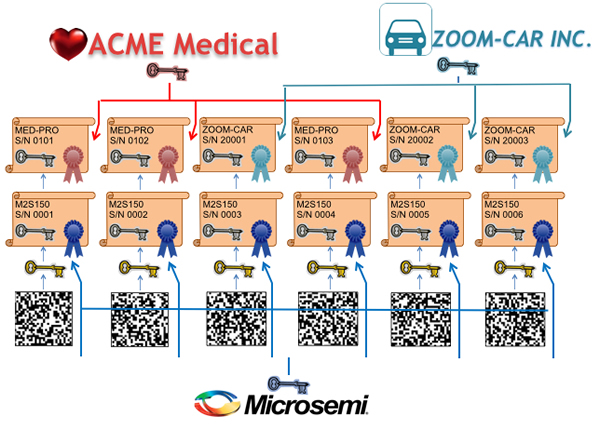
A chain-of-trust is created founded on the unclonable device identity established by the PUF including keys certified by the component manufacturer, allowing each system integrator/operator to certify their own independent PKI so machines they build and use can communicate securely with other machines and servers authorised by them, and no others.
If the message has been tampered with, its digital signature will not verify correctly. The recipient also has to check that the public key it is using is authentic, especially if it was sent with the message and not pre-placed with the recipient. This is done by checking the CA’s digital signature on the X.509 certificate using the CA’s public key, which is generally pre-placed in every device by the manufacturer or network operator, and is inherently trusted. Therefore, a hierarchical certificate-based chain-of-trust is created; the message is proven authentic because the signature applied by the sending device is verified, and the public key used to do this verification is proven authentic because it’s certified by the CA, whose public key is inherently trusted by the way it was originally installed in all the devices. The identity of every legitimate machine in the network can be known with a very high assurance level, and messages can be attributed to these machines with high confidence. Conversely, imposter machines and forged messages can easily be detected.
Some prime examples of open-market devices using PUF technology are the SmartFusion2 SoC FPGA and IGLOO2 FPGA families of components from Microsemi. FPGAs and SoC FPGAs provide many benefits in M2M applications due to their inherent flexibility and high number of I/O pins. The SRAM PUF in these particular FPGAs is used to establish a pre-configured certified identity for each device with Microsemi as the certificate authority. These devices also have built-in cryptographic capabilities such as hardware accelerators for AES, SHA, HMAC and ECC, plus a cryptographic-grade true random bit generator. These capabilities can be used to create a user PKI with the user’s own certificate authority blessing each legitimate machine in the network; each machine having a chain-of-trust from the user’s well-protected root-CA keys all the way down to the high-assurance identity established at the atomic level by the PUF in an included Microsemi FPGA. Together, the PUF and PKI establish a strong identity and association for every machine in the virtual private network. Machines and communications thus protected can be used in M2M and IoT applications safely, securely and with confidence.











