Addressing vulnerability of non-IP wireless protocols
Guillaume Crinon, Innovation Technical Marketing Manager and John Jones, Director of Innovation, Avnet Silica, look at how best to provide end-to-end IoT security.
Internet of Things (IoT) represents a dramatic change in how many facets of modern day society work. Through it, all manner of different devices (such as sensors, smart meters, robots etc.) will be connected to industrial network infrastructure, often in huge numbers. However, worries about security are still putting a question mark over how quickly everything is actually going to proliferate.
Estimates on the number of connected IoT nodes vary, but one thing is certain - in the relatively near future, the figure is going be measured in several tens of billions. Analyst firm IHS, for example, predicts that there will be 30.7 billion IoT nodes in operation by 2020 and, furthermore, this tally will have more than doubled by 2025. In the vast majority of cases, IoT nodes will connect to existing network infrastructure via low power wireless technologies (such as Bluetooth, 802.11x, ZigBee, Z-Wave, etc). Herein lies the problem that enterprises now face - such arrangements leave ample opportunity for security breaches, either in the form of industrial espionage or possibly even malicious attacks.
IoT has been around as a concept for well over a decade (the phrase first being coined in the late 1990s, with some suggesting that the initial idea goes back even further than that). It is really only in the last few years that it has started to become valued as a viable technology though - with a number of different application dynamics having driven demand, as well as the emergence of all the necessary supporting electronics and communication standards.
Put very simply, IoT is going to rely on the transfer of data across an array of different networks, passing from the WLAN to the WAN, then on to IP core, or possibly to the cloud (depending on the nature of the application). For each of these networks there are specific protocol stacks and accompanying security mechanisms in place (as illustrated in Figure 1) - with IPsec relating to IP, 802.11x/ZigBee/Bluetooth attended to by WPA, etc. It must be recognised, however, that this in no way constitutes true end-to-end security. At the moment it is still a piecemeal arrangement with some parts being much better equipped than others to deal with security threats.
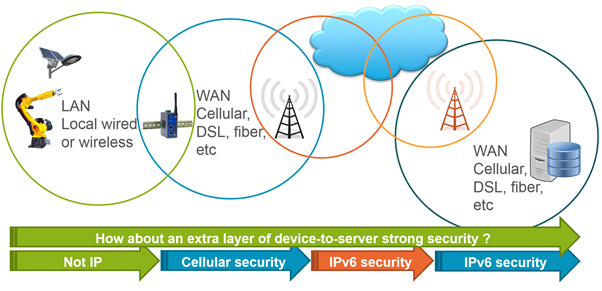
Above: Figure 1. Schematic showing the different networks being utilised and their respective security attributes
Connectivity brings added risks
Now it must be admitted that the continued progression of our connected society is going to have certain, almost unavoidable, security risks associated with it. For example, the emergence in recent years of the ‘Bring Your Own Device’ (BYOD) culture - with company employees connecting their personal laptops, tablets and smartphones to the enterprise network - had serious security implications for IT managers. With the advent of IoT, this is going to be taken a lot further.
The more assets that any enterprise has connected to their network, the greater their exposure to potential security threats will be. Comparatively speaking, BYOD only represents a modest risk, as the number of devices involved is likely to be relatively small and it is within a controlled environment, whereas, the quantity of connected IoT nodes could potentially be vast.
IP version 4 (IPv4) is already starting to be supplanted by IPv6. This enables an exponential increase in the number of available addresses, supports higher speeds and has the benefit of network layer security. Nevertheless, it will take a considerable length time before this is prevalent throughout all aspects of our communication infrastructure. Though in some western countries the penetration of IPv6 can be somewhere between 20 and 40%, elsewhere in the world it is much lower than this (and in some places totally non-existent).
Statistics from Google suggest that currently not much higher than ten percent of global internet traffic can be attributed to IPv6. Now, despite the fact that this is expected to ramp up considerably in the next few years, even then it still will not be in a position to cover the network in its entirety. IPv6 over low power wireless personal area networks (6LoWPAN) is the route via which the IPv6 communication protocol will disseminate into the IoT sphere, but this is still in a relatively nascent phase. As a result the likelihood is that IP-based security is not going to be present in the low power wireless protocols that IoT connectivity will be dependent upon until the 2024/25 timeframe at the earliest.
The modules that make up IoT nodes have a completely different set of characteristics from any other items of hardware connected to an enterprise network (servers, routers, etc). They need to have a compact form factor and low unit cost, as well as exhibiting extremely energy efficient operation (as in many circumstances they will be battery operated and will thus have to adhere to a minimal power budget).
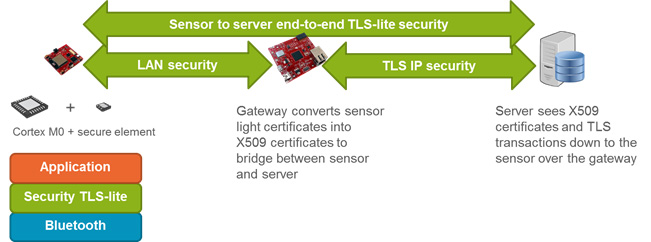
Above: Figure 2. Functional block diagram of Avnet Silica’s microcontroller stack for IoT implementatio:
This consequently affects the way in which their security capabilities are realised. Their bill of materials and size both put restrictions on the memory and processing resources that can be accessed, and this in turn means that there is not sufficient space for storing the sophisticated cryptographic algorithms that need to be applied. With, as already discussed, the incorporation of IP capabilities into lower power wireless protocols still several years away, it is not possible for standard Transport Layer Security (TLS), which relies on IP, to be utilised by IoT nodes.
It is clear, therefore, that security cannot just be confined to a solely IP-centric approach - it has to go beyond this. Now it is not really so daunting a problem for enterprises to cover everything from the server down to the gateway. They have basically been doing this for a very long time. However, there is a major challenge for their engineers when it comes to extending this further, so that the LAN aspect is fully addressed - the ‘last mile’ in the network. They need to find a way to securely connect IoT nodes to IP-based networks using non-IP wireless protocols (such as Bluetooth, etc).
As well as this, another concern is provisioning - whereby the programming of unique identifiers into the IoT node’s memory is carried out in-situ, just prior to connection with the remote server to which it has been allocated. This can be a complicated, time consuming and above all, costly procedure. Furthermore, there is a fundamental flaw in terms of its security, as if it is going to be fully effective, the key that relates to each node should be regularly updated. The more often this happens, the better the protection offered will be. The practicalities of sending operatives out into the field to renew keys means that this rarely (if ever) happens. Yet, without doubt, this compromises network security.
Given that full TLS would be too heavy a strain on low power wireless infrastructure, it has become clear to certain forward-thinking companies in the industry that the best way to overcome this issue is to develop a more streamlined alternative. By employing a rationalised version of TLS that is able to support its most critical functions, the necessary safeguarding of the network can be achieved, but without a large data overhead needing to be factored in. To be deemed completely effective, this would have to be able to deal with mutual authentication between the server and the IoT node, as well as session key distribution etc.
Security partnerships
Avnet Silica has established itself as a partner to customers who need to implement high level security within their networks, and with the roll-out of IoT technology now beginning in earnest it is focusing its efforts on this particular area. Through its cooperation with embedded software specialist Ubiquios, the company has been able to develop a proprietary streamlined microcontroller stack, with related secure element support coming from the team at Trusted Objects. This stack (as detailed in Figure 2) can handle stripped-down TLS derivatives that will be utilised at the network edge. Thanks to it, the specification and sourcing of high performance microcontrollers is no longer needed at gateways. Instead simple Cortex-M0-based units will more than suffice. The systems into which the stack is embedded are thereby destined to be more cost effective and energy efficient, as well as being a lot simpler to implement.
Showcasing this technology is Avnet Silica’s newly introduced security reference design that is able to reach past what standard TLS can achieve. This is based on the company’s Visible Things platform, which comprises tested, proven, secure and highly integrated hardware and advanced embedded software. It relies on cryptography algorithms that have shorter keys (which are ECC-based rather than RSA-based) and therefore have less impact on processing resource and the IoT nodes’ battery reserves. The upshot is that it can provide engineers with an X509 certificate compliant solution that respects the conventions of IP-based security, but in the context of low power wireless connectivity.
In addition, this ground breaking technology significantly simplifies device provisioning. This can have a number of benefits. Firstly, the training that field operatives need will be less, secondly, they will be able to deal with the provisioning of more devices in a day - making the process much quicker to complete and increasing productivity levels. Finally, as devices can be identified directly from the server, the local key can be renewed remotely (rather than needing to send an operative back out to do this manually). This means that sending operatives out into the field no longer needs to even be contemplated. The key associated with each node can be renewed on a regular basis, and a high degree of security thus maintained, without any costs being accrued.
The creation of an architecture where non IP-based nodes can now safely be connected with IP-based networks means that enterprises will be able to have greater confidence in their IoT deployments. It also signifies that the industry is being brought closer than ever to the long term objective of end-to-end security.







