‘Operation Ghoul’ haunts industrial engineering companies
A research team at security firm Kaspersky Lab has issued an alert to businesses in the engineering and industrial sectors about a new wave of cyber attacks that have resulted in systems being infiltrated and data being stolen.
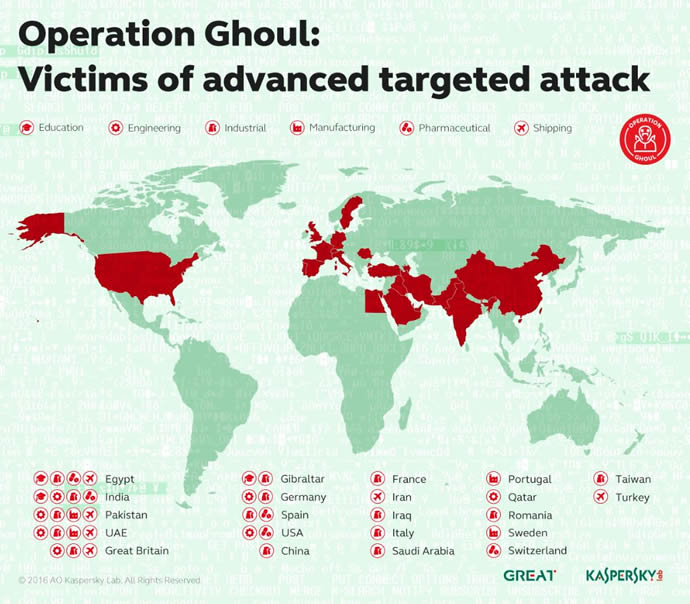
Dubbed Operation Ghoul, the attacks use a combination of malware tools and spear-phishing emails addressed primarily to CEOs, COOs, managers, supervisors, and engineers, and have thus far impacted around 130 organisations across 30 countries, most of which are in the Middle East.
Lane Thames, Software Development Engineer and Security Researcher at IT security company Tripwire commented: “This data illustrates how much of an upper-hand cyber criminals have on the rest of us. No new innovation was used by this attack campaign. Instead, these cyber criminals were using existing malware and phishing emails to infiltrate their victims’ networks. Phishing has long been a valuable technique for cyber criminals because both trained humans and detection software have difficulty identifying a well-crafted phishing email. However, the bigger problem across the board is user awareness.”
While sabotage would seem the obvious motive for cyber attacks against industrial organisations, the Kaspersky researchers have stated that Operation Ghoul appears to be focused more on financial gain – with attacks hacking into the victims’ bank accounts or selling intellectual property to interested parties on the black market.
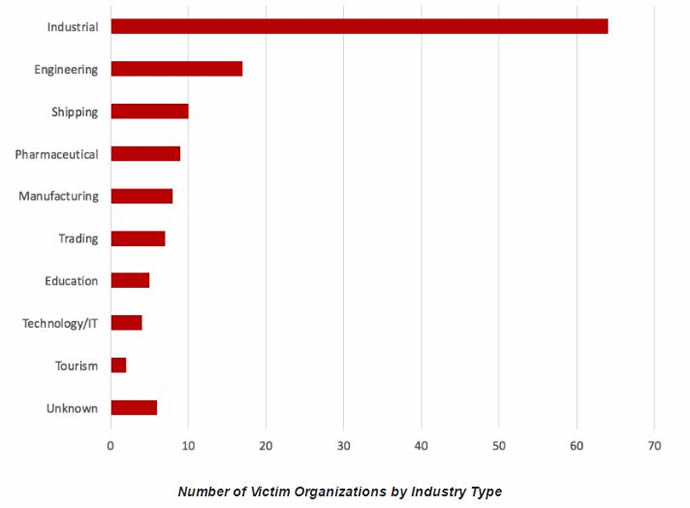
Operation Ghoul is thought to have started in early 2015 and has also infiltrated manufacturing, pharmaceutical and educational organisations. However, Kaspersky has observed that more recent attacks have been more focused, with 70% of the observed attacks in June targeting organisations in the United Arab Emirates (UAE).
Kaspersky highlighted that the Ghoul campaign does not appear to be very sophisticated. For example, attacks tend to use a single command and control server, likely hosted on someone’s compromised machine. However, this doesn’t mean that the attack is not dangerous and, despite the malware’s relative simplicity, most of the attempted hacks have thus far proved successful. Mohamad Amin Hasbini, a Senior Security Researcher for Kaspersky Lab said: “Companies that are not prepared to spot the attacks will sadly suffer.”
Hasbini has posted indicators of compromise on the Kaspersky Lab blog that organisations can use to check their systems for possible infection. He added: “Most infiltrated victim organisations are considered to be SMBs (small to medium size businesses - 30-300 employees). The utilisation of commercial off-the-shelf malware makes the attribution of the attacks more difficult.
“Operation Ghoul is one of the many attacks in the wild targeting industrial, manufacturing and engineering organisations. Kaspersky Lab recommends users to be extra cautious while checking and opening emails and attachments. In addition, privileged users need to be well trained and ready to deal with cyber threats - failure in this is, in most cases, the cause behind private or corporate data leakage, reputation and financial loss.”
The good news is that attacks can be effectively blocked say Kaspersky, and in the case of a breach - quickly remediated, if a proper security strategy is in place in the company affected. While prevention methods (like efficient endpoint security solutions) play the most important role here, they are not the only solutions recommended to enhance protection from attacks like Ghoul. In fact, protection should kick-in before the poisonous e-mail reaches an employee.
The Kaspersky research added that: “The Ghoul campaign is a dangerous targeted attack, but based on the examples from our portfolio we have shown that it can be blocked using existing technologies. Effective deployment of these technologies is what matters. And the key takeaway from this research is that different security methods have to be implemented in a multi-layered fashion. Then, combined, they significantly reduce the chances of a successful attack. They make it much more expensive for threat actors to reach your data.”
Thames concluded: “Organisations should implement training programmes that help their users understand aspects of spam, phishing and malware. A little bit of training can go a long way.”